ccna Discovery 3 : Module 3 exam answers
|
Saturday 18 April 2009
1.
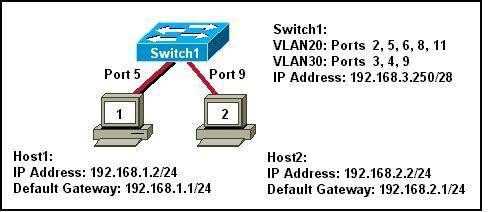
Refer to the exhibit. What two statements can be concluded from the information that is shown in the exhibit? (Choose two.)
• All ports that are listed in the exhibit are access ports.
• ARP requests from Host1 will be forwarded to Host2.
• Attaching Host1 to port 3 will automatically allow communication between both hosts.
• The default gateway for each host must be changed to 192.168.3.250/28 to allow communication between both hosts.
• A router connected to the switch is needed to forward traffic between the hosts.
2.
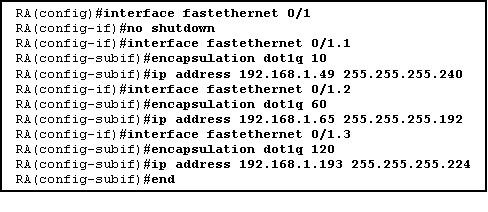
A router is configured to connect to a trunked uplink as shown in the exhibit. A packet is received on the FastEthernet 0/1 physical interface from VLAN 10. The packet destination address is 192.168.1.120. What will the router do with this packet?
• The router will forward the packet out interface FastEthernet 0/1.1 tagged for VLAN 10.
• The router will forward the packet out interface FastEthernet 0/1.2 tagged for VLAN 60.
• The router will forward the packet out interface FastEthernet 0/1.3 tagged for VLAN 60.
• The router will forward the packet out interface FastEthernet 0/1.3 tagged for VLAN 120.
• The router will not process the packet since the source and destination are on the same subnet.
• The router will drop the packet since no network that includes the source address is attached to the router.
3. The information contained in a BPDU is used for which two purposes? (Choose two.)
• to prevent loops by sharing bridging tables between connected switches
• to set the duplex mode of a redundant link
• to determine the shortest path to the root bridge
• to determine which ports will forward frames as part of the spanning tree
• to activate looped paths throughout the network
4. A router has two serial interfaces and two Fast Ethernet interfaces. This router must be connected to a WAN link and to a switch that supports four VLANs. How can this be accomplished in the most efficient and cost-effective manner to support inter-VLAN routing between the four VLANs?
• Connect a smaller router to the serial interface to handle the inter-VLAN traffic.
• Add two additional Fast Ethernet interfaces to the router to allow one VLAN per interface.
• Connect a trunked uplink from the switch to one Fast Ethernet interface on the router and create logical subinterfaces for each VLAN.
• Use serial-to-Fast Ethernet transceivers to connect two of the VLANs to the serial ports on the router. Support the other two VLANs directly to the available FastEthernet ports.
5. When are MAC addresses removed from the CAM table?
• at regular 30 second intervals
• when a broadcast packet is received
• when the IP Address of a host is changed
• after they have been idle for a certain period of time
6.
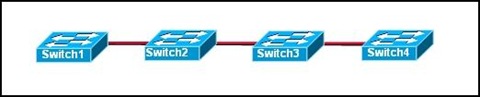
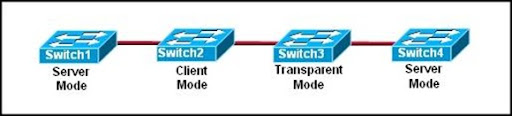
Refer to the exhibit. Switch1 is not participating in the VTP management process with the other switches. Which two are possible reasons for this? (Choose two.)
• Switch2 is in transparent mode.
• Switch1 is in client mode.
• Switch1 is using VTP version 1 and Switch2 is using VTP version 2.
• Switch2 is in server mode.
• Switch1 is in a different management domain.
• Switch1 has no VLANs.
7. Which three must be used when a router interface is configured for VLAN trunking? (Choose three.)
• one subinterface per VLAN
• one physical interface for each subinterface
• one IP network or subnetwork for each subinterface
• one trunked link per VLAN
• a management domain for each subinterface
• a compatible trunking protocol encapsulation for each subinterface
8.
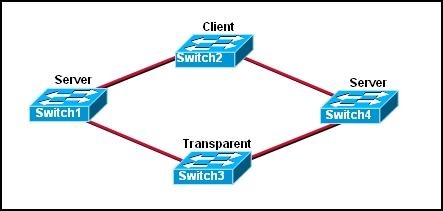
Refer to the exhibit. The switches are connected with trunks within the same VTP management domain. Each switch is labeled with its VTP mode. A new VLAN is added to Switch3. This VLAN does not show up on the other switches. What is the reason for this?
• VLANs cannot be created on transparent mode switches.
• Server mode switches neither listen to nor forward VTP messages from transparent mode switches.
• VLANs created on transparent mode switches are not included in VTP advertisements.
• There are no ports assigned to the new VLAN on the other switches.
• Transparent mode switches do not forward VTP advertisements.
9. Which two criteria are used by STP to select a root bridge? (Choose two.)
• memory size
• bridge priority
• switching speed
• number of ports
• base MAC address
• switch location
10. Which three steps should be taken before moving a Catalyst switch to a new VTP management domain? (Choose three.)
• Reboot the switch.
• Reset the VTP counters to allow the switch to synchronize with the other switches in the domain.
• Download the VTP database from the VTP server in the new domain.
• Configure the VTP server in the domain to recognize the BID of the new switch.
• Select the correct VTP mode and version.
• Configure the switch with the name of the new management domain.
11. Which two items will prevent broadcasts from being sent throughout the network? (Choose two.)
• bridges
• routers
• switches
• VLANs
• hubs
12. Which two characteristics describe a port in the STP blocking state? (Choose two.)
• provides port security
• displays a steady green light
• learns MAC addresses as BPDUs are processed
• discards data frames received from the attached segment
• receives BPDUs and directs them to the system module
13. What is the first step in the process of convergence in a spanning tree topology?
• election of the root bridge
• determination of the designated port for each segment
• blocking of the non-designated ports
• selection of the designated trunk port
• activation of the root port for each segment
14. In which STP state does a switch port transmit user data and learn MAC addresses?
• blocking
• learning
• disabling
• listening
• forwarding
15. What is the purpose of VTP?
• maintaining consistency in VLAN configuration across the network
• routing frames from one VLAN to another
• routing the frames along the best path between switches
• tagging user data frames with VLAN membership information
• distributing BPDUs to maintain loop-free switched paths
16. Which statement best describes adaptive cut-through switching?
• The switch initially forwards all traffic using cut-through switching and then changes to store-and-forward switching if errors exceed a threshold value.
• The switch initially forwards all traffic using cut-through switching and then changes to fast-forward switching if errors exceed a threshold value.
• The switch initially forwards all traffic using cut-through switching and then temporarily disables the port if errors exceed a threshold value.
• The switch initially forwards all traffic using store-and-forward switching and then changes to cut-through switching if errors exceed a threshold value.
17. Using STP, how long does it take for a switch port to go from the blocking state to the forwarding state?
• 2 seconds
• 15 seconds
• 20 seconds
• 50 seconds
18.
Refer to the exhibit. The switches are interconnected by trunked links and are configured for VTP as shown. A new VLAN is added to Switch1. Which three actions will occur? (Choose three.)
• Switch1 will not add the VLAN to its database and will pass the update to Switch 2.
• Switch2 will add the VLAN to its database and pass the update to Switch3.
• Switch3 will pass the VTP update to Switch4.
• Switch3 will add the VLAN to its database.
• Switch4 will add the VLAN to its database.
• Switch4 will not receive the update.
19 Which Catalyst feature causes a switch port to enter the spanning-tree forwarding state immediately?
• backbonefast
• uplinkfast
• portfast
• rapid spanning tree
20.

Refer to the exhibit. Which set of commands would be used on the router to provide communication between the two hosts connected to the switch?
• Router(config)# interface vlan 2
Router(config-if)# ip address 192.168.2.1 255.255.255.0
Router(config-if)# no shutdown
Router(config)# interface vlan 3
Router(config-if)# ip address 192.168.3.1 255.255.255.0
Router(config-if)# no shutdown
• Router(config)# interface fastethernet 0/0
Router(config-if)# no shutdown
Router(config-if)# interface fastethernet 0/0.2
Router(config-subif)# encapsulation dot1q 2
Router(config-subif)# ip address 192.168.2.1 255.255.255.0
Router(config-if)# interface fastethernet 0/0.3
Router(config-subif)# encapsulation dot1q 3
Router(config-subif)# ip address 192.168.3.1 255.255.255.0
• Router(config)# interface vlan 2
Router(config-if)# switchport mode trunk dot1q
Router(config)# interface vlan 3
Router(config-if)# switchport mode trunk dot1q
• Router(config)# interface fastethernet 0/0
Router(config-if)# mode trunk dot1q 2 3
Router(config-if)# ip address 192.168.2.1 255.255.255.0

Refer to the exhibit. What two statements can be concluded from the information that is shown in the exhibit? (Choose two.)
• All ports that are listed in the exhibit are access ports.
• ARP requests from Host1 will be forwarded to Host2.
• Attaching Host1 to port 3 will automatically allow communication between both hosts.
• The default gateway for each host must be changed to 192.168.3.250/28 to allow communication between both hosts.
• A router connected to the switch is needed to forward traffic between the hosts.
2.

A router is configured to connect to a trunked uplink as shown in the exhibit. A packet is received on the FastEthernet 0/1 physical interface from VLAN 10. The packet destination address is 192.168.1.120. What will the router do with this packet?
• The router will forward the packet out interface FastEthernet 0/1.1 tagged for VLAN 10.
• The router will forward the packet out interface FastEthernet 0/1.2 tagged for VLAN 60.
• The router will forward the packet out interface FastEthernet 0/1.3 tagged for VLAN 60.
• The router will forward the packet out interface FastEthernet 0/1.3 tagged for VLAN 120.
• The router will not process the packet since the source and destination are on the same subnet.
• The router will drop the packet since no network that includes the source address is attached to the router.
3. The information contained in a BPDU is used for which two purposes? (Choose two.)
• to prevent loops by sharing bridging tables between connected switches
• to set the duplex mode of a redundant link
• to determine the shortest path to the root bridge
• to determine which ports will forward frames as part of the spanning tree
• to activate looped paths throughout the network
4. A router has two serial interfaces and two Fast Ethernet interfaces. This router must be connected to a WAN link and to a switch that supports four VLANs. How can this be accomplished in the most efficient and cost-effective manner to support inter-VLAN routing between the four VLANs?
• Connect a smaller router to the serial interface to handle the inter-VLAN traffic.
• Add two additional Fast Ethernet interfaces to the router to allow one VLAN per interface.
• Connect a trunked uplink from the switch to one Fast Ethernet interface on the router and create logical subinterfaces for each VLAN.
• Use serial-to-Fast Ethernet transceivers to connect two of the VLANs to the serial ports on the router. Support the other two VLANs directly to the available FastEthernet ports.
5. When are MAC addresses removed from the CAM table?
• at regular 30 second intervals
• when a broadcast packet is received
• when the IP Address of a host is changed
• after they have been idle for a certain period of time
6.

Refer to the exhibit. Switch1 is not participating in the VTP management process with the other switches. Which two are possible reasons for this? (Choose two.)
• Switch2 is in transparent mode.
• Switch1 is in client mode.
• Switch1 is using VTP version 1 and Switch2 is using VTP version 2.
• Switch2 is in server mode.
• Switch1 is in a different management domain.
• Switch1 has no VLANs.
7. Which three must be used when a router interface is configured for VLAN trunking? (Choose three.)
• one subinterface per VLAN
• one physical interface for each subinterface
• one IP network or subnetwork for each subinterface
• one trunked link per VLAN
• a management domain for each subinterface
• a compatible trunking protocol encapsulation for each subinterface
8.

Refer to the exhibit. The switches are connected with trunks within the same VTP management domain. Each switch is labeled with its VTP mode. A new VLAN is added to Switch3. This VLAN does not show up on the other switches. What is the reason for this?
• VLANs cannot be created on transparent mode switches.
• Server mode switches neither listen to nor forward VTP messages from transparent mode switches.
• VLANs created on transparent mode switches are not included in VTP advertisements.
• There are no ports assigned to the new VLAN on the other switches.
• Transparent mode switches do not forward VTP advertisements.
9. Which two criteria are used by STP to select a root bridge? (Choose two.)
• memory size
• bridge priority
• switching speed
• number of ports
• base MAC address
• switch location
10. Which three steps should be taken before moving a Catalyst switch to a new VTP management domain? (Choose three.)
• Reboot the switch.
• Reset the VTP counters to allow the switch to synchronize with the other switches in the domain.
• Download the VTP database from the VTP server in the new domain.
• Configure the VTP server in the domain to recognize the BID of the new switch.
• Select the correct VTP mode and version.
• Configure the switch with the name of the new management domain.
11. Which two items will prevent broadcasts from being sent throughout the network? (Choose two.)
• bridges
• routers
• switches
• VLANs
• hubs
12. Which two characteristics describe a port in the STP blocking state? (Choose two.)
• provides port security
• displays a steady green light
• learns MAC addresses as BPDUs are processed
• discards data frames received from the attached segment
• receives BPDUs and directs them to the system module
13. What is the first step in the process of convergence in a spanning tree topology?
• election of the root bridge
• determination of the designated port for each segment
• blocking of the non-designated ports
• selection of the designated trunk port
• activation of the root port for each segment
14. In which STP state does a switch port transmit user data and learn MAC addresses?
• blocking
• learning
• disabling
• listening
• forwarding
15. What is the purpose of VTP?
• maintaining consistency in VLAN configuration across the network
• routing frames from one VLAN to another
• routing the frames along the best path between switches
• tagging user data frames with VLAN membership information
• distributing BPDUs to maintain loop-free switched paths
16. Which statement best describes adaptive cut-through switching?
• The switch initially forwards all traffic using cut-through switching and then changes to store-and-forward switching if errors exceed a threshold value.
• The switch initially forwards all traffic using cut-through switching and then changes to fast-forward switching if errors exceed a threshold value.
• The switch initially forwards all traffic using cut-through switching and then temporarily disables the port if errors exceed a threshold value.
• The switch initially forwards all traffic using store-and-forward switching and then changes to cut-through switching if errors exceed a threshold value.
17. Using STP, how long does it take for a switch port to go from the blocking state to the forwarding state?
• 2 seconds
• 15 seconds
• 20 seconds
• 50 seconds
18.

Refer to the exhibit. The switches are interconnected by trunked links and are configured for VTP as shown. A new VLAN is added to Switch1. Which three actions will occur? (Choose three.)
• Switch1 will not add the VLAN to its database and will pass the update to Switch 2.
• Switch2 will add the VLAN to its database and pass the update to Switch3.
• Switch3 will pass the VTP update to Switch4.
• Switch3 will add the VLAN to its database.
• Switch4 will add the VLAN to its database.
• Switch4 will not receive the update.
19 Which Catalyst feature causes a switch port to enter the spanning-tree forwarding state immediately?
• backbonefast
• uplinkfast
• portfast
• rapid spanning tree
20.

Refer to the exhibit. Which set of commands would be used on the router to provide communication between the two hosts connected to the switch?
• Router(config)# interface vlan 2
Router(config-if)# ip address 192.168.2.1 255.255.255.0
Router(config-if)# no shutdown
Router(config)# interface vlan 3
Router(config-if)# ip address 192.168.3.1 255.255.255.0
Router(config-if)# no shutdown
• Router(config)# interface fastethernet 0/0
Router(config-if)# no shutdown
Router(config-if)# interface fastethernet 0/0.2
Router(config-subif)# encapsulation dot1q 2
Router(config-subif)# ip address 192.168.2.1 255.255.255.0
Router(config-if)# interface fastethernet 0/0.3
Router(config-subif)# encapsulation dot1q 3
Router(config-subif)# ip address 192.168.3.1 255.255.255.0
• Router(config)# interface vlan 2
Router(config-if)# switchport mode trunk dot1q
Router(config)# interface vlan 3
Router(config-if)# switchport mode trunk dot1q
• Router(config)# interface fastethernet 0/0
Router(config-if)# mode trunk dot1q 2 3
Router(config-if)# ip address 192.168.2.1 255.255.255.0
ccna Discovery 3 : Module 2 exam answers
|
1. What type of connection point is a point of presence (POP)?
• between a client and a host
• between two local networks
• between a computer and a switch
• between an ISP and an Enterprise network
2. A network administrator needs to configure Telnet access to a router. Which group of commandsenable Telnet access to the router?
• Router(config)# enable password class
Router(config)# line con 0
Router(config-line)# login
Router(config-line)# password cisco
• Router(config)# ip host 192.168.1.1 NewYork
Router(config)# enable password cisco
• Router(config)# line aux 0
Router(config-line)# login
Router(config-line)# password cisco
• Router(config)# enable password class
Router(config)# line vty 0 4
Router(config-line)# login
Router(config-line)# password cisco
3. Which two types of information should be included in a business continuity plan? (Choose two.)
• maintenance time periods
• intrusion monitoring records
• offsite data storage procedures
• alternate IT processing locations*
• problem resolution escalation steps
4. Which two router parameters can be set from interface configuration mode? (Choose two.)
• IP address
• Telnet password
• hostname
• console password
• subnet mask
• enable secret password
5. Which two devices protect a corporate network against malicious attacks at the enterprise edge ?(Choose two.)
• demarc
• IP security (IPSec)
• Data Service Unit (DSU)
• intrusion prevention system (IPS)
• intrusion detection system (IDS)
6. Which three steps must be performed to remove all VLAN information from a switch but retain therest of the configuration? (Choose three.)
• Remove all VLAN associations from the interfaces.
• Remove the 802.1q encapsulation from the interfac
• Issue the command copy start run.
• Issue the command delete flash:vlan.dat.
• Issue the command erase start.
• Reload the switch.
7. What is the demarcation?
• physical point where the ISP responsibilty ends and the customer responsibilty begins
• physical location where all server farm connections meet before being distributed into the Core
• point of entry for outside attacks and is often vulnerable
• point of entry for all Access Layer connections from the Distribution Layer devices
8. Which device is responsible for moving packets between multiple network segments?
• router
• switch
• CSU/DSU
• IDS device
10. What information can an administrator learn using the show version command?
• Cisco IOS filename
• configured routing protocol
• status of each interface
• IP addresses of all interfaces
11. Which two situations require a network administrator to use out-of-band management to change arouter configuration? (Choose two.)
• Network links to the router are down.
• No Telnet password has been configured on the router.
• The administrator can only connect to the router using SSH.
• The network interfaces of the router are not configured with IP addresses.
• Company security policy requires that only HTTPS be used to connect to routers.
12. It is crucial that network administrators be able to examine and configure network devices fromtheir homes. Which two approaches allow this connectivity without increasing vulnerability to externalattacks? (Choose two.)
• Configure a special link at the POP to allow external entry from the home computer.
• Set up VPN access between the home computer and the network.
• Install a cable modem in the home to link to the network.
• Configure ACLs on the edge routers that allow only authorized users to access management portson network devices.
• Configure a server in the DMZ with a special username and password to allow external access.
13. A network administrator must define specific business processes to implement if a catastrophicdisaster prevents a company from performing daily business routines. Which portion of the networkdocumentation is the administrator defining?
• business security plan
• business continuity plan
• network solvency plan
• service level agreement
• network maintenance plan
14. A DoS attack crippled the daily operations of a large company for 8 hours. Which two optionscould be implemented by the network administrator to possibly prevent such an attack in the future?(Choose two.)
• install security devices with IDS and IPS at the enterprise edge
• reset all user passwords every 30 days
• filter packets based on IP address, traffic pattern, and protocol
• deny external workers VPN access to internal resources
• ensure critical devices are physically secure and placed behind the demarc
15. A network manager wants to have processes in place to ensure that network upgrades do not affectbusiness operations. What will the network manager create for this purpose?
• business security plan
• business continuity plan
• service level agreement
• network maintenance plan
16. An investment company has multiple servers that hold mission critical datThey are worried that ifsomething happens to these servers, they will lose this valuable information. Which type of plan isneeded for this company to help minimize loss in the event of a server crash?
• business security
• business continuity
• network maintenance
• service level agreement
17. When searching for information about authentication methods and usernames of companypersonnel, where can a network administrator look?
• Business Continuity Plan
• Business Security Plan
• Network Maintenance Plan
• Service Level Agreement
18. Refer to the exhibit. Which statement is true about port Fa5/1?
• When a violation is detected, the port will log the information to a syslog server.
• When a violation is detected, the port will go into err-disable mod
• There have been 11 security violations since the last reloa
• The port is currently in the shutdown state.
• between a client and a host
• between two local networks
• between a computer and a switch
• between an ISP and an Enterprise network
2. A network administrator needs to configure Telnet access to a router. Which group of commandsenable Telnet access to the router?
• Router(config)# enable password class
Router(config)# line con 0
Router(config-line)# login
Router(config-line)# password cisco
• Router(config)# ip host 192.168.1.1 NewYork
Router(config)# enable password cisco
• Router(config)# line aux 0
Router(config-line)# login
Router(config-line)# password cisco
• Router(config)# enable password class
Router(config)# line vty 0 4
Router(config-line)# login
Router(config-line)# password cisco
3. Which two types of information should be included in a business continuity plan? (Choose two.)
• maintenance time periods
• intrusion monitoring records
• offsite data storage procedures
• alternate IT processing locations*
• problem resolution escalation steps
4. Which two router parameters can be set from interface configuration mode? (Choose two.)
• IP address
• Telnet password
• hostname
• console password
• subnet mask
• enable secret password
5. Which two devices protect a corporate network against malicious attacks at the enterprise edge ?(Choose two.)
• demarc
• IP security (IPSec)
• Data Service Unit (DSU)
• intrusion prevention system (IPS)
• intrusion detection system (IDS)
6. Which three steps must be performed to remove all VLAN information from a switch but retain therest of the configuration? (Choose three.)
• Remove all VLAN associations from the interfaces.
• Remove the 802.1q encapsulation from the interfac
• Issue the command copy start run.
• Issue the command delete flash:vlan.dat.
• Issue the command erase start.
• Reload the switch.
7. What is the demarcation?
• physical point where the ISP responsibilty ends and the customer responsibilty begins
• physical location where all server farm connections meet before being distributed into the Core
• point of entry for outside attacks and is often vulnerable
• point of entry for all Access Layer connections from the Distribution Layer devices
8. Which device is responsible for moving packets between multiple network segments?
• router
• switch
• CSU/DSU
• IDS device
10. What information can an administrator learn using the show version command?
• Cisco IOS filename
• configured routing protocol
• status of each interface
• IP addresses of all interfaces
11. Which two situations require a network administrator to use out-of-band management to change arouter configuration? (Choose two.)
• Network links to the router are down.
• No Telnet password has been configured on the router.
• The administrator can only connect to the router using SSH.
• The network interfaces of the router are not configured with IP addresses.
• Company security policy requires that only HTTPS be used to connect to routers.
12. It is crucial that network administrators be able to examine and configure network devices fromtheir homes. Which two approaches allow this connectivity without increasing vulnerability to externalattacks? (Choose two.)
• Configure a special link at the POP to allow external entry from the home computer.
• Set up VPN access between the home computer and the network.
• Install a cable modem in the home to link to the network.
• Configure ACLs on the edge routers that allow only authorized users to access management portson network devices.
• Configure a server in the DMZ with a special username and password to allow external access.
13. A network administrator must define specific business processes to implement if a catastrophicdisaster prevents a company from performing daily business routines. Which portion of the networkdocumentation is the administrator defining?
• business security plan
• business continuity plan
• network solvency plan
• service level agreement
• network maintenance plan
14. A DoS attack crippled the daily operations of a large company for 8 hours. Which two optionscould be implemented by the network administrator to possibly prevent such an attack in the future?(Choose two.)
• install security devices with IDS and IPS at the enterprise edge
• reset all user passwords every 30 days
• filter packets based on IP address, traffic pattern, and protocol
• deny external workers VPN access to internal resources
• ensure critical devices are physically secure and placed behind the demarc
15. A network manager wants to have processes in place to ensure that network upgrades do not affectbusiness operations. What will the network manager create for this purpose?
• business security plan
• business continuity plan
• service level agreement
• network maintenance plan
16. An investment company has multiple servers that hold mission critical datThey are worried that ifsomething happens to these servers, they will lose this valuable information. Which type of plan isneeded for this company to help minimize loss in the event of a server crash?
• business security
• business continuity
• network maintenance
• service level agreement
17. When searching for information about authentication methods and usernames of companypersonnel, where can a network administrator look?
• Business Continuity Plan
• Business Security Plan
• Network Maintenance Plan
• Service Level Agreement
18. Refer to the exhibit. Which statement is true about port Fa5/1?
• When a violation is detected, the port will log the information to a syslog server.
• When a violation is detected, the port will go into err-disable mod
• There have been 11 security violations since the last reloa
• The port is currently in the shutdown state.
ccna Discovery 3 : Module 1 exam answers
|
1. What can be found at the enterprise edge?
• Internet, VPN, and WAN modules
• Internet, PSTN, and WAN services
• server farms and network management
• campus infrastructure, including access layer devices
2. In which functional area of the Cisco Enterprise Architecture should IDS and IPS be located to detect
• and prevent services from accessing hosts?
• Enterprise Campus
• Edge Distribution
• Enterprise Edge
• Service Provider Edge
3. A business consultant must use Internet websites to research a report on the e-business strategies of several firms and then electronically deliver the report to a group of clients in cities throughout the world. Which two teleworker tools can the consultant use to accomplish this project? (Choose two.)
• VoIP
• VPN
• HTTP
• Telnet
• email
4. Which two measures help ensure that a hardware problem does not cause an outage in an enterprise LAN that supports mission critical services? (Choose two.)
• providing failover capability
• installing redundant power supplies
• purchasing more bandwidth from the ISP
• implementing broadcast containment with VLANs
• installing routers that can handle a greater amount of throughput
5. Which task would typically only require services located at the access layer of the hierarchical design model?
• connecting to the corporate web server to update sales figures
• using a VPN from home to send data to the main office servers
• printing a meeting agenda on a local departmental network printer
• placing a VoIP call to a business associate in another country
• responding to an e-mail from a co-worker in another department
6. How does a VPN work to support remote user productivity?
• It uses SSL to encrypt remote user logins to the corporate intranet.
• It uses secure Telnet for remote user connections to internal network devices.
• It creates a virtual circuit that allows real-time communications between any two Internet endpoints.
• It uses encapsulation to create a secure tunnel for transmission of data across non-secure networks.****
7. A remote user needs to access a networking device on the internal network of the company. The transactions between the remote user and the device must be secure. Which protocol enables this to happen securely?
• HTTP
• SSH
• Telnet
• FTP
8. What does VoIP provide to telecommuters?
• high-quality, live-video presentations
• real-time voice communications over the Internet
• ability to share desktop applications simultaneously
• secure, encrypted data transmissions through the Internet
9. Which functional component of the Cisco Enterprise Architecture is responsible for hosting internal servers?
• enterprise campus
• enterprise edge
• service provider edge
• building distribution
10. What is the purpose of the Cisco Enterprise Architecture?
• remove the three-layer hierarchical model and use a flat network approach
• divide the network into functional components while still maintaining the concept of Core, Distribution, and Access Layers
• provide services and functionality to the core layer by grouping various components into a single
• component located in the access layer
• reduce overall network traffic by grouping server farms, the management server, corporate intranet, and e-commerce routers in the same layer
11. Which two solutions would an enterprise IT department use to facilitate secure intranet access for remote workers? (Choose two.)
• VPN
• NAT
• user authentication
• client firewall software
• packet sniffing
12. Which statement describes the difference between an enterprise WAN and an enterprise extranet?
• An enterprise WAN is designed to interconnect local LANs, while an enterprise extranet is designed to interconnect remote branch offices.
• An enterprise WAN is designed to interconnect branch offices, while an enterprise extranet is designed to give access to external business partners.
• An enterprise WAN is designed to provide remote access for its teleworkers, while an enterprise extranet is designed to provide Internet connectivity for the enterprise.
• An enterprise WAN is designed to provide Internet connectivity for the enterprise, while an enterprise extranet is designed to provide remote access to the enterprise network for teleworkers.
13. Why would a network administrator want to limit the size of failure domains when designing a network?
• reduces the effect of Ethernet collisions
• reduces the impact of a key device or service failure
• reduces the impact of Internet congestion on critical traffic
• reduces the impact of blocking broadcast packets at the edge of the local network
14. What is the main purpose of the Access Layer in a hierarchically designed network?
• performs routing and packet manipulation
• supplies redundancy and failover protection
• provides a high-speed, low-latency backbone
• serves as a network connection point for end-user devices
15. Which three functions are performed at the Distribution Layer of the hierarchical network model? (Choose three.)
• forwards traffic that is destined for other networks
• isolates network problems to prevent them from affecting the Core Layer
• allows end users to access the local network
• provides a connection point for separate local networks
• transports large amounts of data between different geographic sites
• forwards traffic to other hosts on the same logical network
16. What is a benefit of having an extranet?
• It provides web-like access to company information for employees only.
• It limits access to corporate information to secure VPN or remote access connections only.
• It allows customers and partners to access company information by connecting to a public web server.
• It allows suppliers and contractors to access confidential internal information using controlled external connections.
17. What are two important characteristics or functions of devices at the Enterprise Edge? (Choose two.)
• providing Internet, telephone, and WAN services to the enterprise network
• providing a connection point for end-user devices to the enterprise network
• providing high-speed backbone connectivity with redundant connections
• providing intrusion detection and intrusion prevention to protect the network against malicious activity
• providing packet inspection to determine if incoming packets should be allowed on the enterprise network
18. Why is TCP the preferred Layer 4 protocol for transmitting data files?
• TCP is more reliable than UDP because it requires lost packets to be retransmitted.
• TCP requires less processing by the source and destination hosts than UDP.
• UDP introduces delays that degrade the quality of the data applications.
• TCP ensures fast delivery because it does not require sequencing or acknowlegements.
19. The ABC Corporation implements the network for its new headquarters using the Cisco Enterprise Architecture. The network administrator wants to filter the traffic from and to the outside world. Where should the administrator deploy a firewall device?
• server farm
• enterprise edge
• enterprise campus
• service provider edge
20. Which two statements are reasons why UDP is used for voice and video traffic instead of TCP?(Choose two.)
• TCP requires all data packets to be delivered for the data to be usable.
• The acknowledgment process of TCP introduces delays that break the streams of data.
• UDP does not have mechanisms for retransmitting lost packets.
• UDP tolerates delays and compensates for them.
• TCP is a connectionless protocol that provides end-to-end reliability.
• UDP is a connection-oriented protocol that provides end-to-end reliability
• Internet, VPN, and WAN modules
• Internet, PSTN, and WAN services
• server farms and network management
• campus infrastructure, including access layer devices
2. In which functional area of the Cisco Enterprise Architecture should IDS and IPS be located to detect
• and prevent services from accessing hosts?
• Enterprise Campus
• Edge Distribution
• Enterprise Edge
• Service Provider Edge
3. A business consultant must use Internet websites to research a report on the e-business strategies of several firms and then electronically deliver the report to a group of clients in cities throughout the world. Which two teleworker tools can the consultant use to accomplish this project? (Choose two.)
• VoIP
• VPN
• HTTP
• Telnet
4. Which two measures help ensure that a hardware problem does not cause an outage in an enterprise LAN that supports mission critical services? (Choose two.)
• providing failover capability
• installing redundant power supplies
• purchasing more bandwidth from the ISP
• implementing broadcast containment with VLANs
• installing routers that can handle a greater amount of throughput
5. Which task would typically only require services located at the access layer of the hierarchical design model?
• connecting to the corporate web server to update sales figures
• using a VPN from home to send data to the main office servers
• printing a meeting agenda on a local departmental network printer
• placing a VoIP call to a business associate in another country
• responding to an e-mail from a co-worker in another department
6. How does a VPN work to support remote user productivity?
• It uses SSL to encrypt remote user logins to the corporate intranet.
• It uses secure Telnet for remote user connections to internal network devices.
• It creates a virtual circuit that allows real-time communications between any two Internet endpoints.
• It uses encapsulation to create a secure tunnel for transmission of data across non-secure networks.****
7. A remote user needs to access a networking device on the internal network of the company. The transactions between the remote user and the device must be secure. Which protocol enables this to happen securely?
• HTTP
• SSH
• Telnet
• FTP
8. What does VoIP provide to telecommuters?
• high-quality, live-video presentations
• real-time voice communications over the Internet
• ability to share desktop applications simultaneously
• secure, encrypted data transmissions through the Internet
9. Which functional component of the Cisco Enterprise Architecture is responsible for hosting internal servers?
• enterprise campus
• enterprise edge
• service provider edge
• building distribution
10. What is the purpose of the Cisco Enterprise Architecture?
• remove the three-layer hierarchical model and use a flat network approach
• divide the network into functional components while still maintaining the concept of Core, Distribution, and Access Layers
• provide services and functionality to the core layer by grouping various components into a single
• component located in the access layer
• reduce overall network traffic by grouping server farms, the management server, corporate intranet, and e-commerce routers in the same layer
11. Which two solutions would an enterprise IT department use to facilitate secure intranet access for remote workers? (Choose two.)
• VPN
• NAT
• user authentication
• client firewall software
• packet sniffing
12. Which statement describes the difference between an enterprise WAN and an enterprise extranet?
• An enterprise WAN is designed to interconnect local LANs, while an enterprise extranet is designed to interconnect remote branch offices.
• An enterprise WAN is designed to interconnect branch offices, while an enterprise extranet is designed to give access to external business partners.
• An enterprise WAN is designed to provide remote access for its teleworkers, while an enterprise extranet is designed to provide Internet connectivity for the enterprise.
• An enterprise WAN is designed to provide Internet connectivity for the enterprise, while an enterprise extranet is designed to provide remote access to the enterprise network for teleworkers.
13. Why would a network administrator want to limit the size of failure domains when designing a network?
• reduces the effect of Ethernet collisions
• reduces the impact of a key device or service failure
• reduces the impact of Internet congestion on critical traffic
• reduces the impact of blocking broadcast packets at the edge of the local network
14. What is the main purpose of the Access Layer in a hierarchically designed network?
• performs routing and packet manipulation
• supplies redundancy and failover protection
• provides a high-speed, low-latency backbone
• serves as a network connection point for end-user devices
15. Which three functions are performed at the Distribution Layer of the hierarchical network model? (Choose three.)
• forwards traffic that is destined for other networks
• isolates network problems to prevent them from affecting the Core Layer
• allows end users to access the local network
• provides a connection point for separate local networks
• transports large amounts of data between different geographic sites
• forwards traffic to other hosts on the same logical network
16. What is a benefit of having an extranet?
• It provides web-like access to company information for employees only.
• It limits access to corporate information to secure VPN or remote access connections only.
• It allows customers and partners to access company information by connecting to a public web server.
• It allows suppliers and contractors to access confidential internal information using controlled external connections.
17. What are two important characteristics or functions of devices at the Enterprise Edge? (Choose two.)
• providing Internet, telephone, and WAN services to the enterprise network
• providing a connection point for end-user devices to the enterprise network
• providing high-speed backbone connectivity with redundant connections
• providing intrusion detection and intrusion prevention to protect the network against malicious activity
• providing packet inspection to determine if incoming packets should be allowed on the enterprise network
18. Why is TCP the preferred Layer 4 protocol for transmitting data files?
• TCP is more reliable than UDP because it requires lost packets to be retransmitted.
• TCP requires less processing by the source and destination hosts than UDP.
• UDP introduces delays that degrade the quality of the data applications.
• TCP ensures fast delivery because it does not require sequencing or acknowlegements.
19. The ABC Corporation implements the network for its new headquarters using the Cisco Enterprise Architecture. The network administrator wants to filter the traffic from and to the outside world. Where should the administrator deploy a firewall device?
• server farm
• enterprise edge
• enterprise campus
• service provider edge
20. Which two statements are reasons why UDP is used for voice and video traffic instead of TCP?(Choose two.)
• TCP requires all data packets to be delivered for the data to be usable.
• The acknowledgment process of TCP introduces delays that break the streams of data.
• UDP does not have mechanisms for retransmitting lost packets.
• UDP tolerates delays and compensates for them.
• TCP is a connectionless protocol that provides end-to-end reliability.
• UDP is a connection-oriented protocol that provides end-to-end reliability
ccna Exploration 3 : Module 4 exam answers
|
1. Refer to the exhibit. Switch1 is not participating in the VTP management process with the other switches shown in the exhibit. What are two possible reasons for this? (Choose two.)
• Switch2 is in transparent mode.
• Switch1 is in client mode.
• Switch1 is using VTP version 1 and Switch2 is using VTP version 2.
• Switch2 is in server mode.
• Switch1 is in a different management domain.
• Switch1 has no VLANs.
2. Refer to the exhibit. Switches SW1 and SW2 are interconnected via a trunk link but failed to exchange VLAN information. The network administrator issued the show vtp status command to troubleshoot the problem. On the basis of the output provided, what could be done to fix the problem?
• The switches must be interconnected via access link.
• Switch SW2 must be configured as a VTP client.
• Both switches must be configured as VTP clients.
• Both switches must be configured with the same VTP revision number.
• The switches must be configured with the same VTP domain name.
3. Refer to the exhibit. Which two facts can be confirmed by this output? (Choose two.)
• If this switch is added to an established network, the other VTP-enabled switches in the same VTP domain will consider their own
• VLAN information to be more recent than the VLAN information advertised by this switch.
• This switch shows no configuration revision errors.
• This switch has established two-way communication with the neighboring devices.
• This switch is configured to advertise its VLAN configuration to other VTP-enabled switches in the same VTP domain.
• This switch is configured to allows the network manager to maximize bandwidth by restricting traffic to specific network devices.
4. Which two statements describe VTP transparent mode operation? (Choose two.)
• Transparent mode switches can create VLAN management information.
• Transparent mode switches can add VLANs of local significance only.
• Transparent mode switches pass any VLAN management information that they receive to other switches.
• Transparent mode switches can adopt VLAN management changes that are received from other switches.
• Transparent mode switches originate updates about the status of their VLANS and inform other switches about that status.
5. Refer to the exhibit. Switch2 was previously used in a lab environment and has been added to the production network in server mode. The lab and production networks use the same VTP domain name, so the network administrator made no configuration changes to Switch2 before adding it to the production network. The lab domain has a higher revision number. After Switch2 was added to the production network, many computers lost network connectivity. What is the quickest way to solve the problem?
• Reset the revision number on Switch2 with either the delete VTP command or by changing the domain name and then changing it back.
• Change Switch1 to transparent VTP mode to reclaim all VLANs in vlan.dat, and then change back to server mode.
• Change Switch2 to client mode so the VLANs will automatically repopulate.
• Re-enter all appropriate VLANs, except VLAN 1, manually on Switch1 so that they repropagate throughout the network.
6. What causes a VTP configured switch to issue a summary advertisement?
• A new host has been attached to a switch in the management domain.
• A port on a switch in the management domain has changed to blocking mode.
• A five-minute update timer has elapsed.
• The advertisement revision number has reached n+1.
7. Which two statements describe VTP client mode operation. (Choose two.)
• can add VLANs of local significance only
• can only adopt VLAN management changes
• can create and adopt updated VLAN management information
• can only pass VLAN management information without adopting changes
• can add VLANs to domain
• cannot add VLANs
8 Which statement is true when VTP is configured on a switched network that incorporates VLANs?
• VTP is only compatible with the 802.1Q standard.
• VTP adds to the complexity of managing a switched network.
• A switch configured for VTP can belong to more than one VTP domain.
• VTP dynamically communicates VLAN additions, deletions and modifications to all switches in the same VTP domain.
• VTP advertisements are passed over access links to other switches.
9. Refer to the exhibit. All switches in the VTP domain are new. Switch SW1 is configured as a VTP server, switches SW2 and SW4 are configured as VTP clients, and switch SW3 is configured in VTP transparent mode. Which switch or switches receive VTP updates and synchronize their VLAN configuration based on those updates?
• All switches receive updates and synchronize VLAN information.
• Only switch SW2 receives updates and synchronizes VLAN information.
• SW3 and SW4 receive updates, but only switch SW4 synchronizes VLAN information.
• Only switches SW3 and SW4 receive updates and synchronize VLAN information.
10. Refer to the exhibit. What information can be learned from the output provided?
• It verifies the configured VTP password.
• It verifies the VTP domain is configured to use VTP version 2.
• It verifies VTP advertisements are being exchanged.
• It verifies the VTP domain name is V1.
11. Which statement is true about the VTP pruning process?
• VTP pruning automatically updates all switches within the VTP domain with VLAN information.
• VTP pruning updates all switches within the VTP domain with information about pruning-eligible VLANs.
• VTP pruning updates all switches within the VTP domain with information about pruning-ineligible VLANs.
• VTP pruning prevents flooded traffic from crossing trunk links to switches that do not need to process the flood traffic.
12. Refer to the exhibit. The switches in the exhibit are connected with trunks within the same VTP management domain. Each switch is labeled with its VTP mode. A new VLAN is added to Switch3. This VLAN does not show up on the other switches. What is the reason for this?
• VLANs cannot be created on transparent mode switches.
• Server mode switches neither listen to nor forward VTP messages from transparent mode switches.
• VLANs created on transparent mode switches are not included in VTP advertisements.
• There are no ports assigned to the new VLAN on the other switches.
• Transparent mode switches do not forward VTP advertisements.
13. What does a client mode switch in a VTP management domain do when it receives a summary advertisement with a revision number higher than its current revision number?
• It suspends forwarding until a subset advertisement update arrives.
• It issues an advertisement request for new VLAN information.
• It increments the revision number and forwards it to other switches.
• It deletes the VLANs not included in the summary advertisement.
• It issues summary advertisements to advise other switches of status changes.
14. Which three VTP parameters must be identical on all switches to participate in the same VTP domain? (Choose three.)
• revision number
• domain name
• pruning
• mode
• domain password
• version number
15. Refer to the exhibit. All switches in the network participate in the same VTP domain. What happens when the new switch SW2 with a default configuration and revision number of 0 is inserted in the existing VTP domain Lab Network?
• The switch operates as a VTP client.
• switch operates in VTP transparent mode.
• The switch operates as a VTP server and deletes the existing VLAN configuration in the domain.
• The switch operates as a VTP server, but does not impact the existing VLAN configuration in the domain.
16. Refer to the exhibit. Switch S1 is in VTP server mode. Switches S2 and S3 are in client mode. An administrator accidentally disconnects the cable from F0/1 on S2. What will the effect be?
• S2 loses all VLANs until the cable is reconnected.
• S2 automatically transitions to VTP transparent mode.
• S2 does not send a VTP request advertisement unless it is reloaded.
• S2 automatically sends a VTP request advertisement to 172.17.99.11 when the cable is reconnected.
17. Which two statements are true about the implementation of VTP? (Choose two.)
• Switches must be connected via trunks.
• The VTP domain name is case sensitive.
• Transparent mode switches cannot be configured with new VLANs.
• The VTP password is mandatory and case sensitive.
• Switches that use VTP must have the same switch name
• Switch2 is in transparent mode.
• Switch1 is in client mode.
• Switch1 is using VTP version 1 and Switch2 is using VTP version 2.
• Switch2 is in server mode.
• Switch1 is in a different management domain.
• Switch1 has no VLANs.
2. Refer to the exhibit. Switches SW1 and SW2 are interconnected via a trunk link but failed to exchange VLAN information. The network administrator issued the show vtp status command to troubleshoot the problem. On the basis of the output provided, what could be done to fix the problem?
• The switches must be interconnected via access link.
• Switch SW2 must be configured as a VTP client.
• Both switches must be configured as VTP clients.
• Both switches must be configured with the same VTP revision number.
• The switches must be configured with the same VTP domain name.
3. Refer to the exhibit. Which two facts can be confirmed by this output? (Choose two.)
• If this switch is added to an established network, the other VTP-enabled switches in the same VTP domain will consider their own
• VLAN information to be more recent than the VLAN information advertised by this switch.
• This switch shows no configuration revision errors.
• This switch has established two-way communication with the neighboring devices.
• This switch is configured to advertise its VLAN configuration to other VTP-enabled switches in the same VTP domain.
• This switch is configured to allows the network manager to maximize bandwidth by restricting traffic to specific network devices.
4. Which two statements describe VTP transparent mode operation? (Choose two.)
• Transparent mode switches can create VLAN management information.
• Transparent mode switches can add VLANs of local significance only.
• Transparent mode switches pass any VLAN management information that they receive to other switches.
• Transparent mode switches can adopt VLAN management changes that are received from other switches.
• Transparent mode switches originate updates about the status of their VLANS and inform other switches about that status.
5. Refer to the exhibit. Switch2 was previously used in a lab environment and has been added to the production network in server mode. The lab and production networks use the same VTP domain name, so the network administrator made no configuration changes to Switch2 before adding it to the production network. The lab domain has a higher revision number. After Switch2 was added to the production network, many computers lost network connectivity. What is the quickest way to solve the problem?
• Reset the revision number on Switch2 with either the delete VTP command or by changing the domain name and then changing it back.
• Change Switch1 to transparent VTP mode to reclaim all VLANs in vlan.dat, and then change back to server mode.
• Change Switch2 to client mode so the VLANs will automatically repopulate.
• Re-enter all appropriate VLANs, except VLAN 1, manually on Switch1 so that they repropagate throughout the network.
6. What causes a VTP configured switch to issue a summary advertisement?
• A new host has been attached to a switch in the management domain.
• A port on a switch in the management domain has changed to blocking mode.
• A five-minute update timer has elapsed.
• The advertisement revision number has reached n+1.
7. Which two statements describe VTP client mode operation. (Choose two.)
• can add VLANs of local significance only
• can only adopt VLAN management changes
• can create and adopt updated VLAN management information
• can only pass VLAN management information without adopting changes
• can add VLANs to domain
• cannot add VLANs
8 Which statement is true when VTP is configured on a switched network that incorporates VLANs?
• VTP is only compatible with the 802.1Q standard.
• VTP adds to the complexity of managing a switched network.
• A switch configured for VTP can belong to more than one VTP domain.
• VTP dynamically communicates VLAN additions, deletions and modifications to all switches in the same VTP domain.
• VTP advertisements are passed over access links to other switches.
9. Refer to the exhibit. All switches in the VTP domain are new. Switch SW1 is configured as a VTP server, switches SW2 and SW4 are configured as VTP clients, and switch SW3 is configured in VTP transparent mode. Which switch or switches receive VTP updates and synchronize their VLAN configuration based on those updates?
• All switches receive updates and synchronize VLAN information.
• Only switch SW2 receives updates and synchronizes VLAN information.
• SW3 and SW4 receive updates, but only switch SW4 synchronizes VLAN information.
• Only switches SW3 and SW4 receive updates and synchronize VLAN information.
10. Refer to the exhibit. What information can be learned from the output provided?
• It verifies the configured VTP password.
• It verifies the VTP domain is configured to use VTP version 2.
• It verifies VTP advertisements are being exchanged.
• It verifies the VTP domain name is V1.
11. Which statement is true about the VTP pruning process?
• VTP pruning automatically updates all switches within the VTP domain with VLAN information.
• VTP pruning updates all switches within the VTP domain with information about pruning-eligible VLANs.
• VTP pruning updates all switches within the VTP domain with information about pruning-ineligible VLANs.
• VTP pruning prevents flooded traffic from crossing trunk links to switches that do not need to process the flood traffic.
12. Refer to the exhibit. The switches in the exhibit are connected with trunks within the same VTP management domain. Each switch is labeled with its VTP mode. A new VLAN is added to Switch3. This VLAN does not show up on the other switches. What is the reason for this?
• VLANs cannot be created on transparent mode switches.
• Server mode switches neither listen to nor forward VTP messages from transparent mode switches.
• VLANs created on transparent mode switches are not included in VTP advertisements.
• There are no ports assigned to the new VLAN on the other switches.
• Transparent mode switches do not forward VTP advertisements.
13. What does a client mode switch in a VTP management domain do when it receives a summary advertisement with a revision number higher than its current revision number?
• It suspends forwarding until a subset advertisement update arrives.
• It issues an advertisement request for new VLAN information.
• It increments the revision number and forwards it to other switches.
• It deletes the VLANs not included in the summary advertisement.
• It issues summary advertisements to advise other switches of status changes.
14. Which three VTP parameters must be identical on all switches to participate in the same VTP domain? (Choose three.)
• revision number
• domain name
• pruning
• mode
• domain password
• version number
15. Refer to the exhibit. All switches in the network participate in the same VTP domain. What happens when the new switch SW2 with a default configuration and revision number of 0 is inserted in the existing VTP domain Lab Network?
• The switch operates as a VTP client.
• switch operates in VTP transparent mode.
• The switch operates as a VTP server and deletes the existing VLAN configuration in the domain.
• The switch operates as a VTP server, but does not impact the existing VLAN configuration in the domain.
16. Refer to the exhibit. Switch S1 is in VTP server mode. Switches S2 and S3 are in client mode. An administrator accidentally disconnects the cable from F0/1 on S2. What will the effect be?
• S2 loses all VLANs until the cable is reconnected.
• S2 automatically transitions to VTP transparent mode.
• S2 does not send a VTP request advertisement unless it is reloaded.
• S2 automatically sends a VTP request advertisement to 172.17.99.11 when the cable is reconnected.
17. Which two statements are true about the implementation of VTP? (Choose two.)
• Switches must be connected via trunks.
• The VTP domain name is case sensitive.
• Transparent mode switches cannot be configured with new VLANs.
• The VTP password is mandatory and case sensitive.
• Switches that use VTP must have the same switch name
ccna Exploration 3 : Module 3 exam answers
|
1. What statement about the 802.1q trunking protocol is true?
• 802.1q is Cisco proprietary.
• 802.1q frames are mapped to VLANs by MAC address.
• 802.1q does NOT require the FCS of the original frame to be recalculated.
• 802.1q will not perform operations on frames that are forwarded out access ports.
2. Which two statements describe the benefits of VLANs? (Choose two.)
• VLANs improve network performance by regulating flow control and window size.
• VLANs enable switches to route packets to remote networks via VLAN ID filtering.
• VLANs reduce network cost by reducing the number of physical ports required on switches.
• VLANs improve network security by isolating users that have access to sensitive data and applications.
• VLANs divide a network into smaller logical networks, resulting in lower susceptibility to broadcast storms.
3. What are two characteristics of VLAN1 in a default switch configuration? (Choose two.)
• VLAN1 should renamed.
• VLAN 1 is the management VLAN.
• All switch ports are members of VLAN1.
• Only switch port 0/1 is assigned to VLAN1.
• Links between switches must be members of VLAN1.
4. Refer to the exhibit. SW1 and SW2 are new switches being installed in the topology shown in the exhibit. Interface Fa0/1 on switch SW1 has been configured with trunk mode “on”. Which statement is true about forming a trunk link between the switches SW1 and SW2?
• Interface Fa0/2 on switch SW2 will negotiate to become a trunk link if it supports DTP.
• Interface Fa0/2 on switch SW2 can only become a trunk link if statically configured as a trunk.
• Interface Fa0/1 converts the neighboring link on the adjacent switch into a trunk link if the neighboring interface is configured in nonegotiate mode.
• Interface Fa0/1 converts the neighboring link on the adjacent switch into a trunk link automatically with no consideration of the configuration on the neighboring interface.
5. Refer to the exhibit. Computer 1 sends a frame to computer 4. On which links along the path between computer 1 and computer 4 will a VLAN ID tag be included with the frame?
• A
• A, B
• A, B, D, G
• A, D, F
• C, E
• C, E, F
6. The network administrator wants to separate hosts in Building A into two VLANs numbered 20 and 30. Which two statements are true concerning VLAN configuration? (Choose two.)
• The VLANs may be named.
• VLAN information is saved in the startup configuration.
• Non-default VLANs created manually must use the extended range VLAN numbers.
• The network administrator may create the VLANs in either global configuration mode or VLAN database mode.
• Both VLANs may be named BUILDING_A to distinguish them from other VLANs in different geographical locations.
7. Refer to the exhibit. Which two conclusions can be drawn regarding the switch that produced the output shown? (Choose two.)
• The network administrator configured VLANs 1002-1005.
• The VLANs are in the active state and are in the process of negotiating configuration parameters.
• A FDDI trunk has been configured on this switch.
• The command switchport access vlan 20 was entered in interface configuration mode for Fast Ethernet interface 0/1.
• Devices attached to ports fa0/5 through fa0/8 cannot communicate with devices attached to ports fa0/9 through fa0/12 without the use of a Layer 3 device.
8. What happens to the member ports of a VLAN when the VLAN is deleted?
• The ports cannot communicate with other ports.
• The ports default back to the management VLAN.
• The ports automatically become a part of VLAN1.
• The ports remain a part of that VLAN until the switch is rebooted. They then become members of the management VLAN.
9. A network administrator is removing several VLANs from a switch. When the administrator enters the no vlan 1 command, an error is received. Why did this command generate an error?
• VLAN 1 can never be deleted.
• VLAN 1 can only be deleted by deleting the vlan.dat file.
• VLAN 1 can not be deleted until all ports have been removed from it.
• VLAN 1 can not be deleted until another VLAN has been assigned its responsibilities.
10. What is the effect of the switchport mode dynamic desirable command?
• DTP cannot negotiate the trunk since the native VLAN is not the default VLAN.
• The remote connected interface cannot negotiate a trunk unless it is also configured as dynamic desirable.
• The connected devices dynamically determine when data for multiple VLANs must be transmitted across the link and bring the trunk up as needed.
• A trunk link is formed if the remote connected device is configured with the switchport mode dynamic auto or switchport mode trunk commands.
11. Refer to the exhibit. The exhibited configurations do not allow the switches to form a trunk. What is the most likely cause of this problem?
• Cisco switches only support the ISL trunking protocol.
• The trunk cannot be negotiated with both ends set to auto.
• By default, Switch1 will only allow VLAN 5 across the link.
• A common native VLAN should have been configured on the switches.
12. Switch port fa0/1 was manually configured as a trunk, but now it will be used to connect a host to the network. How should the network administrator reconfigure switch port Fa0/1?
• Disable DTP.
• Delete any VLANs currently being trunked through port Fa0/1.
• Administratively shut down and re-enable the interface to return it to default.
• Enter the switchport mode access command in interface configuration mode.
13. Refer to the exhibit. Computer B is unable to communicate with computer D. What is the most likely cause of this problem?
• The link between the switches is up but not trunked.
• VLAN 3 is not an allowed VLAN to enter the trunk between the switches.
• The router is not properly configured to route traffic between the VLANs.
• Computer D does not have a proper address for the VLAN 3 address space.
14. Refer to the exhibit. The network administrator has just added VLAN 50 to Switch1 and Switch2 and assigned hosts on the IP addresses of the VLAN in the 10.1.50.0/24 subnet range. Computer A can communicate with computer B, but not with computer C or computer D. What is the most likely cause of this problem?
• There is a native VLAN mismatch.
• The link between Switch1 and Switch2 is up but not trunked.
• The router is not properly configured for inter-VLAN routing.
• VLAN 50 is not allowed to entering the trunk between Switch1 and Switch2.
15. Refer to the exhibit. Which statement is true concerning interface Fa0/5?
• The default native VLAN is being used.
• The trunking mode is set to auto.
• Trunking can occur with non-Cisco switches.
• VLAN information about the interface encapsulates the Ethernet frames.
16. What statements describe how hosts on VLANs communicate?
• Hosts on different VLANs use VTP to negotiate a trunk.
• Hosts on different VLANs communicate through routers.
• Hosts on different VLANs should be in the same IP network.
• Hosts on different VLANs examine VLAN ID in the frame tagging to determine if the frame for their network.
• 17. Refer to the exhibit. How far is a broadcast frame that is sent by computer A propagated in the LAN domain?
• none of the computers will receive the broadcast frame
• computer A, computer B, computer C
• computer A, computer D, computer G
• computer B, computer C
• computer D, computer G
• computer A, computer B, computer C, computer D, computer E, computer F, computer G, computer H, computer I
18. What is a valid consideration for planning VLAN traffic across multiple switches?
• Configuring interswitch connections as trunks will cause all hosts on any VLAN to receive broadcasts from the other VLANs.
• A trunk connection is affected by broadcast storms on any particular VLAN that is carried by that trunk.
• Restricting trunk connections between switches to a single VLAN will improve efficiency of port usage.
• Carrying all required VLANs on a single access port will ensure proper traffic separation.
19. Which two statements about the 802.1q trunking protocol are true? (Choose two.)
• 802.1q is Cisco proprietary.
• 802.1q frames are mapped to VLANs by MAC address.
• If 802.1q is used on a frame, the FCS must be recalculated.
• 802.1q will not perform operations on frames that are forwarded out access ports.
• 802.1q allows the encapsulation of the original frame to identify the VLAN from which a frame originated.
20. What switch port modes will allow a switch to successfully form a trunking link if the neighboring switch port is in "dynamic desirable" mode?
• dynamic desirable mode
• on or dynamic desirable mode
• on, auto, or dynamic desirable mode
• on, auto, dynamic desirable, or nonegotiate mode
21. Refer to the exhibit. Company HR is adding PC4, a specialized application workstation, to a new company office. The company will add a switch, S3, connected via a trunk link to S2, another switch. For security reasons the new PC will reside in the HR VLAN, VLAN 10. The new office will use the 172.17.11.0/24 subnet. After installation, the existing PCs are unable to access shares on PC4. What is the likely cause?
• The switch to switch connection must be configured as an access port to permit access to VLAN 10 on S3.
• The new PC is on a different subnet so Fa0/2 on S3 must be configured as a trunk port.
• PC4 must use the same subnet as the other HR VLAN PCs.
• A single VLAN cannot span multiple switches.
22. What must the network administrator do to remove Fast Ethernet port fa0/1 from VLAN 2 and assign it to VLAN 3?
• Enter the no vlan 2 and the vlan 3 commands in global configuration mode.
• Enter the switchport access vlan 3 command in interface configuration mode.
• Enter the switchport trunk native vlan 3 command in interface configuration mode.
• Enter the no shutdown in interface configuration mode to return it to the default configuration and then configure the port for VLAN 3
• 802.1q is Cisco proprietary.
• 802.1q frames are mapped to VLANs by MAC address.
• 802.1q does NOT require the FCS of the original frame to be recalculated.
• 802.1q will not perform operations on frames that are forwarded out access ports.
2. Which two statements describe the benefits of VLANs? (Choose two.)
• VLANs improve network performance by regulating flow control and window size.
• VLANs enable switches to route packets to remote networks via VLAN ID filtering.
• VLANs reduce network cost by reducing the number of physical ports required on switches.
• VLANs improve network security by isolating users that have access to sensitive data and applications.
• VLANs divide a network into smaller logical networks, resulting in lower susceptibility to broadcast storms.
3. What are two characteristics of VLAN1 in a default switch configuration? (Choose two.)
• VLAN1 should renamed.
• VLAN 1 is the management VLAN.
• All switch ports are members of VLAN1.
• Only switch port 0/1 is assigned to VLAN1.
• Links between switches must be members of VLAN1.
4. Refer to the exhibit. SW1 and SW2 are new switches being installed in the topology shown in the exhibit. Interface Fa0/1 on switch SW1 has been configured with trunk mode “on”. Which statement is true about forming a trunk link between the switches SW1 and SW2?
• Interface Fa0/2 on switch SW2 will negotiate to become a trunk link if it supports DTP.
• Interface Fa0/2 on switch SW2 can only become a trunk link if statically configured as a trunk.
• Interface Fa0/1 converts the neighboring link on the adjacent switch into a trunk link if the neighboring interface is configured in nonegotiate mode.
• Interface Fa0/1 converts the neighboring link on the adjacent switch into a trunk link automatically with no consideration of the configuration on the neighboring interface.
5. Refer to the exhibit. Computer 1 sends a frame to computer 4. On which links along the path between computer 1 and computer 4 will a VLAN ID tag be included with the frame?
• A
• A, B
• A, B, D, G
• A, D, F
• C, E
• C, E, F
6. The network administrator wants to separate hosts in Building A into two VLANs numbered 20 and 30. Which two statements are true concerning VLAN configuration? (Choose two.)
• The VLANs may be named.
• VLAN information is saved in the startup configuration.
• Non-default VLANs created manually must use the extended range VLAN numbers.
• The network administrator may create the VLANs in either global configuration mode or VLAN database mode.
• Both VLANs may be named BUILDING_A to distinguish them from other VLANs in different geographical locations.
7. Refer to the exhibit. Which two conclusions can be drawn regarding the switch that produced the output shown? (Choose two.)
• The network administrator configured VLANs 1002-1005.
• The VLANs are in the active state and are in the process of negotiating configuration parameters.
• A FDDI trunk has been configured on this switch.
• The command switchport access vlan 20 was entered in interface configuration mode for Fast Ethernet interface 0/1.
• Devices attached to ports fa0/5 through fa0/8 cannot communicate with devices attached to ports fa0/9 through fa0/12 without the use of a Layer 3 device.
8. What happens to the member ports of a VLAN when the VLAN is deleted?
• The ports cannot communicate with other ports.
• The ports default back to the management VLAN.
• The ports automatically become a part of VLAN1.
• The ports remain a part of that VLAN until the switch is rebooted. They then become members of the management VLAN.
9. A network administrator is removing several VLANs from a switch. When the administrator enters the no vlan 1 command, an error is received. Why did this command generate an error?
• VLAN 1 can never be deleted.
• VLAN 1 can only be deleted by deleting the vlan.dat file.
• VLAN 1 can not be deleted until all ports have been removed from it.
• VLAN 1 can not be deleted until another VLAN has been assigned its responsibilities.
10. What is the effect of the switchport mode dynamic desirable command?
• DTP cannot negotiate the trunk since the native VLAN is not the default VLAN.
• The remote connected interface cannot negotiate a trunk unless it is also configured as dynamic desirable.
• The connected devices dynamically determine when data for multiple VLANs must be transmitted across the link and bring the trunk up as needed.
• A trunk link is formed if the remote connected device is configured with the switchport mode dynamic auto or switchport mode trunk commands.
11. Refer to the exhibit. The exhibited configurations do not allow the switches to form a trunk. What is the most likely cause of this problem?
• Cisco switches only support the ISL trunking protocol.
• The trunk cannot be negotiated with both ends set to auto.
• By default, Switch1 will only allow VLAN 5 across the link.
• A common native VLAN should have been configured on the switches.
12. Switch port fa0/1 was manually configured as a trunk, but now it will be used to connect a host to the network. How should the network administrator reconfigure switch port Fa0/1?
• Disable DTP.
• Delete any VLANs currently being trunked through port Fa0/1.
• Administratively shut down and re-enable the interface to return it to default.
• Enter the switchport mode access command in interface configuration mode.
13. Refer to the exhibit. Computer B is unable to communicate with computer D. What is the most likely cause of this problem?
• The link between the switches is up but not trunked.
• VLAN 3 is not an allowed VLAN to enter the trunk between the switches.
• The router is not properly configured to route traffic between the VLANs.
• Computer D does not have a proper address for the VLAN 3 address space.
14. Refer to the exhibit. The network administrator has just added VLAN 50 to Switch1 and Switch2 and assigned hosts on the IP addresses of the VLAN in the 10.1.50.0/24 subnet range. Computer A can communicate with computer B, but not with computer C or computer D. What is the most likely cause of this problem?
• There is a native VLAN mismatch.
• The link between Switch1 and Switch2 is up but not trunked.
• The router is not properly configured for inter-VLAN routing.
• VLAN 50 is not allowed to entering the trunk between Switch1 and Switch2.
15. Refer to the exhibit. Which statement is true concerning interface Fa0/5?
• The default native VLAN is being used.
• The trunking mode is set to auto.
• Trunking can occur with non-Cisco switches.
• VLAN information about the interface encapsulates the Ethernet frames.
16. What statements describe how hosts on VLANs communicate?
• Hosts on different VLANs use VTP to negotiate a trunk.
• Hosts on different VLANs communicate through routers.
• Hosts on different VLANs should be in the same IP network.
• Hosts on different VLANs examine VLAN ID in the frame tagging to determine if the frame for their network.
• 17. Refer to the exhibit. How far is a broadcast frame that is sent by computer A propagated in the LAN domain?
• none of the computers will receive the broadcast frame
• computer A, computer B, computer C
• computer A, computer D, computer G
• computer B, computer C
• computer D, computer G
• computer A, computer B, computer C, computer D, computer E, computer F, computer G, computer H, computer I
18. What is a valid consideration for planning VLAN traffic across multiple switches?
• Configuring interswitch connections as trunks will cause all hosts on any VLAN to receive broadcasts from the other VLANs.
• A trunk connection is affected by broadcast storms on any particular VLAN that is carried by that trunk.
• Restricting trunk connections between switches to a single VLAN will improve efficiency of port usage.
• Carrying all required VLANs on a single access port will ensure proper traffic separation.
19. Which two statements about the 802.1q trunking protocol are true? (Choose two.)
• 802.1q is Cisco proprietary.
• 802.1q frames are mapped to VLANs by MAC address.
• If 802.1q is used on a frame, the FCS must be recalculated.
• 802.1q will not perform operations on frames that are forwarded out access ports.
• 802.1q allows the encapsulation of the original frame to identify the VLAN from which a frame originated.
20. What switch port modes will allow a switch to successfully form a trunking link if the neighboring switch port is in "dynamic desirable" mode?
• dynamic desirable mode
• on or dynamic desirable mode
• on, auto, or dynamic desirable mode
• on, auto, dynamic desirable, or nonegotiate mode
21. Refer to the exhibit. Company HR is adding PC4, a specialized application workstation, to a new company office. The company will add a switch, S3, connected via a trunk link to S2, another switch. For security reasons the new PC will reside in the HR VLAN, VLAN 10. The new office will use the 172.17.11.0/24 subnet. After installation, the existing PCs are unable to access shares on PC4. What is the likely cause?
• The switch to switch connection must be configured as an access port to permit access to VLAN 10 on S3.
• The new PC is on a different subnet so Fa0/2 on S3 must be configured as a trunk port.
• PC4 must use the same subnet as the other HR VLAN PCs.
• A single VLAN cannot span multiple switches.
22. What must the network administrator do to remove Fast Ethernet port fa0/1 from VLAN 2 and assign it to VLAN 3?
• Enter the no vlan 2 and the vlan 3 commands in global configuration mode.
• Enter the switchport access vlan 3 command in interface configuration mode.
• Enter the switchport trunk native vlan 3 command in interface configuration mode.
• Enter the no shutdown in interface configuration mode to return it to the default configuration and then configure the port for VLAN 3
ccna Discovery 2 : Final exam answers
|
1 . A company is developing an Internet store for its website. Which protocol should be used to transfer credit card information from customers to the company web server?
• FTPS
• HTTP
• HTTPS
• WEP2
• TFTP
2.
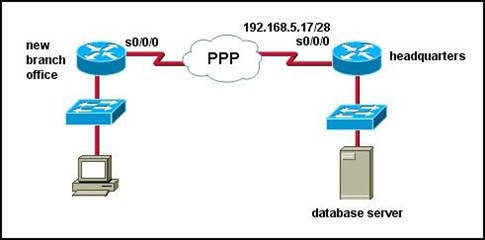
Refer to the exhibit. A new branch office has been added to the corporate network and a new router is to be installed to allow branch office users to access the database server at headquarters. How should the serial 0/0/0 interface of the new branch office router be configured to connect to the headquarters router?
• branch_23(config-if)# ip address 192.168.5.19 255.255.255.240
branch_23(config-if)# no shutdown
• branch_23(config-if)# encapsulation hdlc
branch_23(config-if)# ip address 192.168.5.25 255.255.255.240
branch_23(config-if)# no shutdown
• branch_23(config-if)# encapsulation ppp
branch_23(config-if)# no shutdown
• branch_23(config-if)# encapsulation ppp
branch_23(config-if)# ip address 192.168.5.33 255.255.255.240
• branch_23(config-if)# encapsulation ppp
branch_23(config-if)# ip address 192.168.5.21 255.255.255.240
branch_23(config-if)# no shutdown
3. Which two commands ensure that any password that permits access to the privileged EXEC mode is not shown in plain text when the configuration files are displayed? (Choose two.)
• Router(config)# enable secret cisco
• Router(config)# enable cisco
• Router(config)# encryption-password all
• Router(config)# enable login encrypted
• Router(config)# enable password encryption
• Router(config)# service password-encryption
4. A new network is to be configured on a router. Which of the following tasks must be completed to configure this interface and implement dynamic IP routing for the new network? (Choose three.)
• Select the routing protocol to be configured.
• Assign an IP address and subnet mask to the interface
• Update the ip host configuration information with the device name and new interface IP address.
• Configure the routing protocol with the new network IP address.
• Configure the routing protocol with the new interface IP address and subnet mask.
• Configure the routing protocol in use on all other enterprise routers with the new network information.
5. How does TCP ensure the reliable transfer of data?
• if data segments are not received from the source, the destination requests that the segments be resent.
• If an acknowledgment of the transmitted segments is not received from the destination in a predetermined amount of the time, the source resends the data. • TCP uses the SYN-ACK portion of the three-way handshake to ensure that all data has been received.
• The TCP Protocol Interpreter process verifies the transmitted data at source and destination.
6. A network administrator is asked to design a system to allow simultaneous access to the Internet for 250 users. The ISP for this network can only supply five public IPs. What can be used to accomplish this task?
• routable translation
• dynamic translation
• static translation
• port address translation
7. What is the most commonly used exterior routing protocol?
• BGP
• RIP
• OSPF
• EIGRP
8.
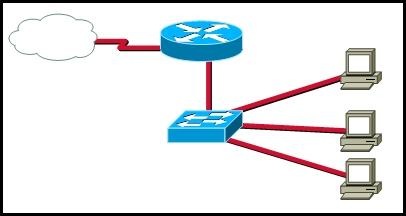
Refer to the exhibit. The network administrator needs to configure the router with a name. Which command will the administrator use to configure the router name?
• Router# ip hostname Boise
• Router# enable hostname Boise
• Router(config-line)# name Boise
• Router(config)# hostname Boise
• Router(config)# ip hostname Boise
9. Why are port numbers included in the TCP header of a segment?
• to indicate the correct router interface that should be used to forward a segment
• to identify which switch ports should receive or forward the segment
• to determine which Layer 3 protocol should be used to encapsulate the data
• to enable a receiving host to forward the data to the appropriate application
• to allow the receiving host to assemble the packet in the proper order
10. What is the purpose of the routing process?
• to encapsulate data that is used to communicate across a network
• to select the paths that are used to direct traffic to destination networks
• to convert a URL name into an IP address
• to provide secure Internet file transfer
• to forward traffic on the basis of MAC addresses
11. Which two statements are true about the use of the debug ip rip command on a Cisco router? (Choose two.)
• The debug ip rip command displays RIP routing activity in real time.
• The debug ip rip command can be issued at the user EXEC configuration mode.
• The debug ip rip command displays a combination of the information that is displayed by the show ip route and show ip protocols commands.
• Because of router processor usage, the debug ip rip command should be used only when necessary.
• The debug ip rip command should be used instead of the show ip route command whenever possible.
12. What minimum configurations must be set on a host to allow a request to be sent to http://www.cisco.com/? (Choose four.)
• DNS server
• WINS server
• IP address
• NetBIOS
• subnet mask
• default gateway
13. A Catalyst 2960 switch has been taken out of storage to be used as a temporary replacement for another switch that needs to be repaired. About a minute after the switch has started, the SYST LED on the front of the switch transitions from blinking green to amber. What is the meaning of the amber SYST LED?
• The switch has no configuration file in NVRAM.
• The switch has failed POST and must be sent for service.
• The switch is functioning properly.
• The switch is in half-duplex mode.
14.
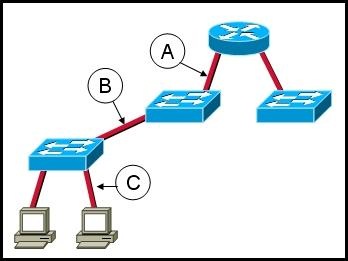
Refer to the exhibit. Which combination of cables and symbols is correct?
• A - crossover, B - straight-through, C - straight-through
• A - crossover, B - rollover, C - straight-through
• A - straight-through, B -crossover, C - straight-through
• A - straight-through, B -straight-through, C - straight-through
• A - straight-through, B - straight-through, C - crossover
• A - rollover, B - straight-through, C - straight-through
15. After an unsuccessful ping to the local router, the technician decides to investigate the router. The technician observes that the lights and fan on the router are not operational. In which layer of the OSI model is the problem most likely occurring?
• transport
• network
• data link
• physical
16. What are three characteristics of the TCP protocol? (Choose three.)
• exchanges datagrams unreliably
• is used to send IP error messages
• forces the retransmission of unacknowledged packets
• creates a virtual session between end-user applications
• carries the IP address of the destination host in the TCP header
• is responsible for breaking messages into segments and reassembling them at their destination
17.
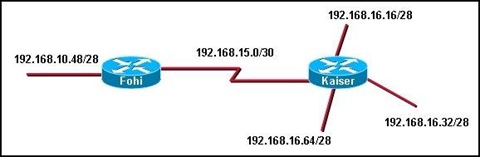 Refer to the exhibit. The network shown is connected using services from the same ISP. How will the Fohi router dynamically learn routes to the 192.168.16.16/28, 192.168.16.32/28, and 192.168.16.64/28 subnetworks?
Refer to the exhibit. The network shown is connected using services from the same ISP. How will the Fohi router dynamically learn routes to the 192.168.16.16/28, 192.168.16.32/28, and 192.168.16.64/28 subnetworks?
• with BGP
• with a static route
• with a directly connected route
• with an interior routing protocol
18.
Refer to the exhibit. Which type of UTP cable should be used to connect Host A to Switch1?
• rollover
• console
• crossover
• straight-through
19 When customers use credit cards to make purchases at a small business, a modem is heard dialing a telephone number to transfer the transaction data to the central office. What type of WAN serial connection is in use?
• leased line
• packet switched
• circuit switched
• point-to-point
20. A user reports being unable to access the Internet. The help desk technician employs a bottom-up approach to troubleshooting. The technician first has the user check the patch cable connection from the PC to the wall, and then has the user verify that the NIC has a green link light. What will the technician have the user do next?
• Enter an IP address into the WWW browser address bar to see if DNS is at fault.
• Use traceroute to identify the device along the path to the ISP that may be at fault.
• Verify the IP address, subnet, and gateway settings using ipconfig on the PC .
• Connect to the user home router to check firewall settings for blocked TCP ports.
21.
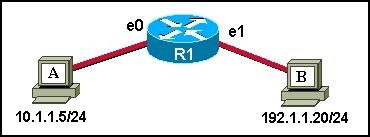
A ping 192.1.1.20 command is issued on workstation A to determine if workstation B can be reached. What events will occur if this command is successful? (Choose two.)
• The router will block the ping request message.
• The router will reply to the echo request with a proxy ping response.
• Workstation A will send a UDP ping request message to workstation B.
• Workstation B will send a UDP ping reply message to workstation A.
• Workstation A will send an ICMP echo request message to workstation B.
• Workstation B will send an ICMP echo reply message to workstation A.
22. How does a router know of paths to destination networks? (Choose two.)
• inspection of the destination IP address in data packets
• ARP requests from connected routers
• manual configuration of routes
• updates from other routers
• DHCP information broadcasts
• updates from the SMTP management information base
23.
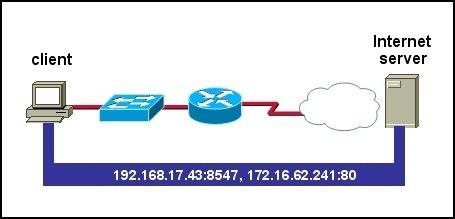
Refer to the exhibit. Which two statements describe the data conversation shown? (Choose two.)
• The data conversation was started by the HTTP application process running on the client.
• The data conversation is identified by TCP port 80 on the client.
• The user started the data conversation by sending an e-mail.
• The IP address of the Internet server is 192.168.17.43 .
• The Internet server will send data to port 8547 on the client.
24. What is one purpose of the TCP three-way handshake?
• sending echo requests from the source to the destination host to establish the presence of the destination
• determining the IP address of the destination host in preparation for data transfer
• requesting the destination to transfer a binary file to the source
• synchronizing sequence numbers between source and destination in preparation for data transfer
25. Which type of address is 192.168.17.111/28?
• host address
• network address
• broadcast address
• multicast address
26. A customer reports connectivity problems to an ISP technician. Upon questioning the customer, the technician discovers that all network applications are functioning except for FTP. What should the technician suspect is the problem?
• misconfigured firewall
• bad port on switch or hub
• misconfigured IP addressing on the customer's workstation
• wrong DNS server configured on the customer's workstation
• wrong default gateway configured on the customer's workstation
27.

The show ip route command was executed on one of the routers shown in the graphic and the following output was displayed:
C 192.168.4.0/24 is directly connected, Serial0/0
R 192.168.5.0/24 [120/1] via 192.168.4.2, 00:00:19, Serial0/0
R 192.168.1.0/24 [120/2] via 192.168.3.1, 00:00:20, Serial0/1
R 192.168.2.0/24 [120/2] via 192.168.3.1, 00:00:20, Serial0/1
C 192.168.3.0/24 is directly connected, Serial0/1
From which router was this command executed?
• A
• B
• C
• D
28. Refer to the exhibit. Which two sets of commands are required to configure passwords for all management ports on a Catalyst 2960 switch? (Choose two.)
• ALSwitch(config)# interface vlan 1
ALSwitch(config-if)# password cisco
ALSwitch(config-if)# login
• ALSwitch(config)# line vty 0 4
ALSwitch(config-line)# password cisco
ALSwitch(config-line)# login
• ALSwitch(config)# line vty 0 15
ALSwitch(config-line)# password cisco
ALSwitch(config-line)# login
• ALSwitch(config)# enable secret class
ALSwitch(config)# enable password cisco
• ALSwitch(config)# interface fa0/1
ALSwitch(config-if)# password cisco
ALSwitch(config-if)# no shutdown
• ALSwitch(config)# line cons 0
ALSwitch(config-line)# password cisco
ALSwitch(config-line)# login
29. A user reports being able to access the Internet but not being able to download e-mail from the mail server at the ISP. What should the user check on the user workstation?
• the POP3 and SMTP server settings in the e-mail application
• the patch cable connections at the back of the workstation and at the wall plate
• the DHCP settings in the operating system
• the IP address, mask, and default gateway values
• the NIC drivers
30.
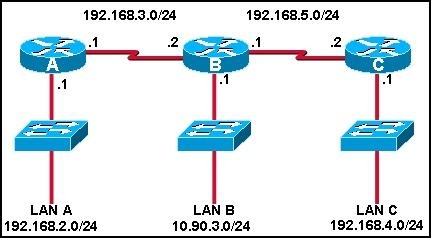
Refer to the graphic. Which command will configure a static route on Router A to direct traffic from LAN A that is destined for LAN C?
• RouterA(config)# ip route 192.168.4.0 255.255.255.0 192.168.5.2
• RouterA(config)# ip route 192.168.4.0 255.255.255.0 192.168.3.2
• RouterA(config)# ip route 192.168.5.0 255.255.255.0 192.168.3.2
• RouterA(config)# ip route 192.168.3.0 255.255.255.0 192.168.3.1
• RouterA(config)# ip route 192.168.3.2 255.255.255.0 192.168.4.0
31. Which subnet masks could be used when subnetting a Class B IP address? (Choose two.)
• 255.255.255.240
• 255.255.192.0
• 255.255.0.0
• 255.192.0.0
• 240.0.0.0
• 255.0.0.0
32.
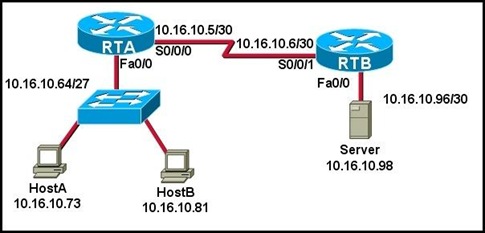
Refer to the exhibit. The network administrator has configured the RTA and RTB interfaces. In order to allow hosts that are attached to RTA to reach the server that is attached to RTB, a static route from RTA to the server LAN and a default route from RTB back to RTA need to be configured. Which two commands will the administrator use to accomplish these tasks on the two routers? (Choose two.)
• RTA(config)# ip route 10.16.10.5 255.255.255.252 10.16.10.6
• RTA(config)# ip route 0.0.0.0 0.0.0.0 10.16.10.6
• RTA(config)# ip route 10.16.10.96 255.255.255.252 10.16.10.6
• RTB(config)# ip route 10.16.10.6 255.255.255.248 10.16.10.6
• RTB(config)# ip route 0.0.0.0 0.0.0.0 S0/0/1
• RTB(config)# ip route 0.0.0.0 0.0.0.0 10.16.10.6
33. How do port filtering and access lists help provide network security?
• They prevent specified types of traffic from reaching specified network destinations.
• They alert network administrators to various type of denial of service attacks as they occur.
• They prevent viruses, worms, and Trojans from infecting host computers and servers.
• They enable encryption and authentication of confidential data communications.
34.
Refer to the exhibit. The network administrator of the building in the graphic needs to choose the type of cable best suited to add ServerB to the network. Which cable type is the best choice?
• STP
• UTP
• coaxial
• fiber optic
35. What is used by a routing protocol to determine the best path to include in the routing table?
• Convergence time
• Default distance
• Metric
• Type of router
36.
Refer to the exhibit. Which IP addresses could be assigned to the hosts in the diagram? (Choose two.)
• 192.168.65.31
• 192.168.65.32
• 192.168.65.35
• 192.168.65.60
• 192.168.65.63
• 192.168.65.64
37.
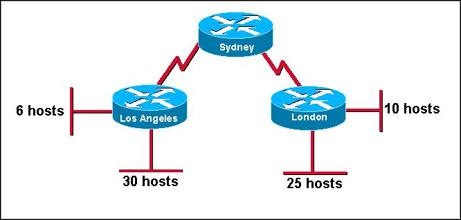
Given the network 192.168.25.0 shown in the graphic, which subnet mask would accommodate the number of hosts in each subnet?
• 255.255.0.0
• 255.255.224.0
• 255.255.255.0
• 255.255.255.224
• 255.255.255.240
• 255.255.255.248
38. Which two protocols allow network devices to report their status and events to a centralized network management device? (Choose two.)
• Syslog
• Telnet
• HTTP
• HTTPS
• SNMP
39. What is true regarding the differences between NAT and PAT?
• PAT uses the word "overload" at the end of the access-list statement to share a single registered address.
• Static NAT allows an unregistered address to map to multiple registered addresses.
• Dynamic NAT allows hosts to receive the same global address each time external access is required.
• PAT uses unique source port numbers to distinguish between translations.
40.
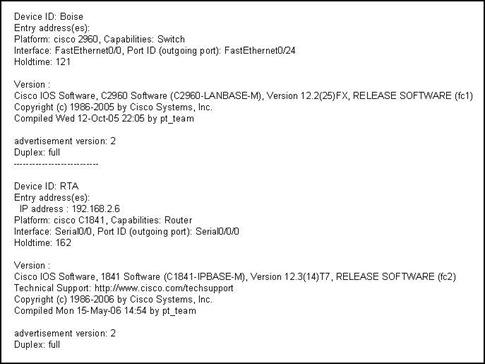
Refer to the exhibit. The graphic shows the output of a command issued on router RTB. According to the output, what two statements are true of router RTB? (Choose two.)
• The router is connected to a router named Boise.
• Router RTB is connected to a Cisco 1841 router.
• Router RTB is directly connected to two other routers.
• The IP address of the router interface connected to router RTB is 192.168.2.6 .
• The RTB router is connected to two Cisco devices by Fast Ethernet links.
41.
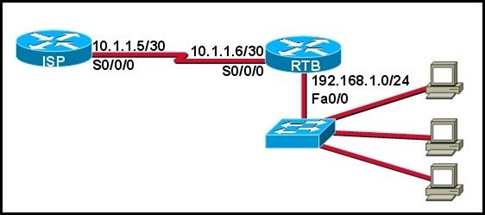
Refer to the exhibit. The network administrator uses the command below to configure a default route to the ISP network : RTB(config)# ip route 0.0.0.0 0.0.0.0 10.1.1.6 A ping issued from the ISP is successful to router RTB. However, ping echo request packets arrive at a host that is attached to the Fa0/0 interface of RTB, and the replies do not make it back to the ISP router. What will fix this problem?
• The ISP must be configured to forward packets from the 192.168.1.0 network.
• The ip route command needs to be edited so that the next hop address is 10.1.1.5.
• The ip route command needs to be edited so that the 192.168.1.1 address is the next hop address.
• The ip route command should be removed from the RTB router configuration.
42. A network technician is using a network management station to gather data about the performance of devices and links within the ISP. Which application layer protocol makes this possible?
• SNMP
• FTP
• DHCP
• SMTP
43. What are two purposes of DNS? (Choose two.)
• to dynamically assign IP addressing information to network hosts
• to simplify the administration of host and default gateway addressing on client computers
• to assign TCP port numbers to hosts as part of the data transfer process
• to resolve human-readable domain names to numeric IP addresses
• to replace the static HOSTS file with a more practical dynamic system
44. A hacker attempts to reach confidential information that is stored on a server inside the corporate network. A network security solution inspects the entire packet, determines that it is a threat, and blocks the packet from entering the inside network. Which security measure protected the network?
• an IDS
• an IPS
• a host-based firewall
• Anti-X software
45. How many host addresses may be assigned on each subnetwork when using the 130.68.0.0 network address with a subnet mask of 255.255.248.0?
• 30
• 256
• 2046
• 2048
• 4094
• 4096
46. In an IPv4 environment, what information is used by the router to forward data packets from one interface of a router to another?
• destination network address
• source network address
• source MAC address
• well known port destination address
47. A small tire retailer requires a low-cost WAN connection to its headquarters in order to manage its inventory and process customer sales in real time. Which WAN connection type is best suited to its needs?
• Sonet
• T3
• dialup
• DSL
• leased line
48. The command copy tftp running-config has been entered on the router. What will this command do?
• copy the configuration in RAM to a server
• copy the configuration file from a server to RAM
• copy the configuration file in NVRAM to RAM
• copy the configuration file in NVRAM to a server
• copy the configuration file from a server to NVRAM
49.
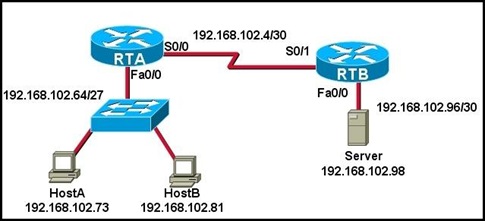
Refer to the exhibit. The network administrator needs to configure the Fa0/0 interface of RTB so that hosts from RTA can connect to the server that is attached to RTB. Which two commands will the administrator use to accomplish this task? (Choose two.)
• RTB# ip address 192.168.102.98 255.255.255.248
• RTB(config-if)# ip address 192.168.102.99 255.255.255.252
• RTB(config)# ip address 192.168.102.97 255.255.255.252
• RTB(config)# no shutdown
• RTB(config-if)# no shutdown
• RTB(config-if)# ip address 192.168.102.97 255.255.255.252
50.
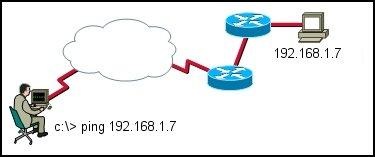
Refer to the exhibit. A NOC technician at an ISP enters the command shown. What are two reasons to use this command? (Choose two.)
• to map the path to 192.168.1.7
• to test reachability to 192.168.1.7
• to locate connectivity problems along the route to 192.168.1.7
• to identify the ISPs that interconnect the NOC with the remote host with the address 192.168.1.7
• to measure the time that packets take to reach 192.168.1.7 and return to the technician's workstation
• FTPS
• HTTP
• HTTPS
• WEP2
• TFTP
2.

Refer to the exhibit. A new branch office has been added to the corporate network and a new router is to be installed to allow branch office users to access the database server at headquarters. How should the serial 0/0/0 interface of the new branch office router be configured to connect to the headquarters router?
• branch_23(config-if)# ip address 192.168.5.19 255.255.255.240
branch_23(config-if)# no shutdown
• branch_23(config-if)# encapsulation hdlc
branch_23(config-if)# ip address 192.168.5.25 255.255.255.240
branch_23(config-if)# no shutdown
• branch_23(config-if)# encapsulation ppp
branch_23(config-if)# no shutdown
• branch_23(config-if)# encapsulation ppp
branch_23(config-if)# ip address 192.168.5.33 255.255.255.240
• branch_23(config-if)# encapsulation ppp
branch_23(config-if)# ip address 192.168.5.21 255.255.255.240
branch_23(config-if)# no shutdown
3. Which two commands ensure that any password that permits access to the privileged EXEC mode is not shown in plain text when the configuration files are displayed? (Choose two.)
• Router(config)# enable secret cisco
• Router(config)# enable cisco
• Router(config)# encryption-password all
• Router(config)# enable login encrypted
• Router(config)# enable password encryption
• Router(config)# service password-encryption
4. A new network is to be configured on a router. Which of the following tasks must be completed to configure this interface and implement dynamic IP routing for the new network? (Choose three.)
• Select the routing protocol to be configured.
• Assign an IP address and subnet mask to the interface
• Update the ip host configuration information with the device name and new interface IP address.
• Configure the routing protocol with the new network IP address.
• Configure the routing protocol with the new interface IP address and subnet mask.
• Configure the routing protocol in use on all other enterprise routers with the new network information.
5. How does TCP ensure the reliable transfer of data?
• if data segments are not received from the source, the destination requests that the segments be resent.
• If an acknowledgment of the transmitted segments is not received from the destination in a predetermined amount of the time, the source resends the data. • TCP uses the SYN-ACK portion of the three-way handshake to ensure that all data has been received.
• The TCP Protocol Interpreter process verifies the transmitted data at source and destination.
6. A network administrator is asked to design a system to allow simultaneous access to the Internet for 250 users. The ISP for this network can only supply five public IPs. What can be used to accomplish this task?
• routable translation
• dynamic translation
• static translation
• port address translation
7. What is the most commonly used exterior routing protocol?
• BGP
• RIP
• OSPF
• EIGRP
8.

Refer to the exhibit. The network administrator needs to configure the router with a name. Which command will the administrator use to configure the router name?
• Router# ip hostname Boise
• Router# enable hostname Boise
• Router(config-line)# name Boise
• Router(config)# hostname Boise
• Router(config)# ip hostname Boise
9. Why are port numbers included in the TCP header of a segment?
• to indicate the correct router interface that should be used to forward a segment
• to identify which switch ports should receive or forward the segment
• to determine which Layer 3 protocol should be used to encapsulate the data
• to enable a receiving host to forward the data to the appropriate application
• to allow the receiving host to assemble the packet in the proper order
10. What is the purpose of the routing process?
• to encapsulate data that is used to communicate across a network
• to select the paths that are used to direct traffic to destination networks
• to convert a URL name into an IP address
• to provide secure Internet file transfer
• to forward traffic on the basis of MAC addresses
11. Which two statements are true about the use of the debug ip rip command on a Cisco router? (Choose two.)
• The debug ip rip command displays RIP routing activity in real time.
• The debug ip rip command can be issued at the user EXEC configuration mode.
• The debug ip rip command displays a combination of the information that is displayed by the show ip route and show ip protocols commands.
• Because of router processor usage, the debug ip rip command should be used only when necessary.
• The debug ip rip command should be used instead of the show ip route command whenever possible.
12. What minimum configurations must be set on a host to allow a request to be sent to http://www.cisco.com/? (Choose four.)
• DNS server
• WINS server
• IP address
• NetBIOS
• subnet mask
• default gateway
13. A Catalyst 2960 switch has been taken out of storage to be used as a temporary replacement for another switch that needs to be repaired. About a minute after the switch has started, the SYST LED on the front of the switch transitions from blinking green to amber. What is the meaning of the amber SYST LED?
• The switch has no configuration file in NVRAM.
• The switch has failed POST and must be sent for service.
• The switch is functioning properly.
• The switch is in half-duplex mode.
14.

Refer to the exhibit. Which combination of cables and symbols is correct?
• A - crossover, B - straight-through, C - straight-through
• A - crossover, B - rollover, C - straight-through
• A - straight-through, B -crossover, C - straight-through
• A - straight-through, B -straight-through, C - straight-through
• A - straight-through, B - straight-through, C - crossover
• A - rollover, B - straight-through, C - straight-through
15. After an unsuccessful ping to the local router, the technician decides to investigate the router. The technician observes that the lights and fan on the router are not operational. In which layer of the OSI model is the problem most likely occurring?
• transport
• network
• data link
• physical
16. What are three characteristics of the TCP protocol? (Choose three.)
• exchanges datagrams unreliably
• is used to send IP error messages
• forces the retransmission of unacknowledged packets
• creates a virtual session between end-user applications
• carries the IP address of the destination host in the TCP header
• is responsible for breaking messages into segments and reassembling them at their destination
17.
 Refer to the exhibit. The network shown is connected using services from the same ISP. How will the Fohi router dynamically learn routes to the 192.168.16.16/28, 192.168.16.32/28, and 192.168.16.64/28 subnetworks?
Refer to the exhibit. The network shown is connected using services from the same ISP. How will the Fohi router dynamically learn routes to the 192.168.16.16/28, 192.168.16.32/28, and 192.168.16.64/28 subnetworks? • with BGP
• with a static route
• with a directly connected route
• with an interior routing protocol
18.

Refer to the exhibit. Which type of UTP cable should be used to connect Host A to Switch1?
• rollover
• console
• crossover
• straight-through
19 When customers use credit cards to make purchases at a small business, a modem is heard dialing a telephone number to transfer the transaction data to the central office. What type of WAN serial connection is in use?
• leased line
• packet switched
• circuit switched
• point-to-point
20. A user reports being unable to access the Internet. The help desk technician employs a bottom-up approach to troubleshooting. The technician first has the user check the patch cable connection from the PC to the wall, and then has the user verify that the NIC has a green link light. What will the technician have the user do next?
• Enter an IP address into the WWW browser address bar to see if DNS is at fault.
• Use traceroute to identify the device along the path to the ISP that may be at fault.
• Verify the IP address, subnet, and gateway settings using ipconfig on the PC .
• Connect to the user home router to check firewall settings for blocked TCP ports.
21.

A ping 192.1.1.20 command is issued on workstation A to determine if workstation B can be reached. What events will occur if this command is successful? (Choose two.)
• The router will block the ping request message.
• The router will reply to the echo request with a proxy ping response.
• Workstation A will send a UDP ping request message to workstation B.
• Workstation B will send a UDP ping reply message to workstation A.
• Workstation A will send an ICMP echo request message to workstation B.
• Workstation B will send an ICMP echo reply message to workstation A.
22. How does a router know of paths to destination networks? (Choose two.)
• inspection of the destination IP address in data packets
• ARP requests from connected routers
• manual configuration of routes
• updates from other routers
• DHCP information broadcasts
• updates from the SMTP management information base
23.

Refer to the exhibit. Which two statements describe the data conversation shown? (Choose two.)
• The data conversation was started by the HTTP application process running on the client.
• The data conversation is identified by TCP port 80 on the client.
• The user started the data conversation by sending an e-mail.
• The IP address of the Internet server is 192.168.17.43 .
• The Internet server will send data to port 8547 on the client.
24. What is one purpose of the TCP three-way handshake?
• sending echo requests from the source to the destination host to establish the presence of the destination
• determining the IP address of the destination host in preparation for data transfer
• requesting the destination to transfer a binary file to the source
• synchronizing sequence numbers between source and destination in preparation for data transfer
25. Which type of address is 192.168.17.111/28?
• host address
• network address
• broadcast address
• multicast address
26. A customer reports connectivity problems to an ISP technician. Upon questioning the customer, the technician discovers that all network applications are functioning except for FTP. What should the technician suspect is the problem?
• misconfigured firewall
• bad port on switch or hub
• misconfigured IP addressing on the customer's workstation
• wrong DNS server configured on the customer's workstation
• wrong default gateway configured on the customer's workstation
27.

The show ip route command was executed on one of the routers shown in the graphic and the following output was displayed:
C 192.168.4.0/24 is directly connected, Serial0/0
R 192.168.5.0/24 [120/1] via 192.168.4.2, 00:00:19, Serial0/0
R 192.168.1.0/24 [120/2] via 192.168.3.1, 00:00:20, Serial0/1
R 192.168.2.0/24 [120/2] via 192.168.3.1, 00:00:20, Serial0/1
C 192.168.3.0/24 is directly connected, Serial0/1
From which router was this command executed?
• A
• B
• C
• D
28. Refer to the exhibit. Which two sets of commands are required to configure passwords for all management ports on a Catalyst 2960 switch? (Choose two.)
• ALSwitch(config)# interface vlan 1
ALSwitch(config-if)# password cisco
ALSwitch(config-if)# login
• ALSwitch(config)# line vty 0 4
ALSwitch(config-line)# password cisco
ALSwitch(config-line)# login
• ALSwitch(config)# line vty 0 15
ALSwitch(config-line)# password cisco
ALSwitch(config-line)# login
• ALSwitch(config)# enable secret class
ALSwitch(config)# enable password cisco
• ALSwitch(config)# interface fa0/1
ALSwitch(config-if)# password cisco
ALSwitch(config-if)# no shutdown
• ALSwitch(config)# line cons 0
ALSwitch(config-line)# password cisco
ALSwitch(config-line)# login
29. A user reports being able to access the Internet but not being able to download e-mail from the mail server at the ISP. What should the user check on the user workstation?
• the POP3 and SMTP server settings in the e-mail application
• the patch cable connections at the back of the workstation and at the wall plate
• the DHCP settings in the operating system
• the IP address, mask, and default gateway values
• the NIC drivers
30.

Refer to the graphic. Which command will configure a static route on Router A to direct traffic from LAN A that is destined for LAN C?
• RouterA(config)# ip route 192.168.4.0 255.255.255.0 192.168.5.2
• RouterA(config)# ip route 192.168.4.0 255.255.255.0 192.168.3.2
• RouterA(config)# ip route 192.168.5.0 255.255.255.0 192.168.3.2
• RouterA(config)# ip route 192.168.3.0 255.255.255.0 192.168.3.1
• RouterA(config)# ip route 192.168.3.2 255.255.255.0 192.168.4.0
31. Which subnet masks could be used when subnetting a Class B IP address? (Choose two.)
• 255.255.255.240
• 255.255.192.0
• 255.255.0.0
• 255.192.0.0
• 240.0.0.0
• 255.0.0.0
32.

Refer to the exhibit. The network administrator has configured the RTA and RTB interfaces. In order to allow hosts that are attached to RTA to reach the server that is attached to RTB, a static route from RTA to the server LAN and a default route from RTB back to RTA need to be configured. Which two commands will the administrator use to accomplish these tasks on the two routers? (Choose two.)
• RTA(config)# ip route 10.16.10.5 255.255.255.252 10.16.10.6
• RTA(config)# ip route 0.0.0.0 0.0.0.0 10.16.10.6
• RTA(config)# ip route 10.16.10.96 255.255.255.252 10.16.10.6
• RTB(config)# ip route 10.16.10.6 255.255.255.248 10.16.10.6
• RTB(config)# ip route 0.0.0.0 0.0.0.0 S0/0/1
• RTB(config)# ip route 0.0.0.0 0.0.0.0 10.16.10.6
33. How do port filtering and access lists help provide network security?
• They prevent specified types of traffic from reaching specified network destinations.
• They alert network administrators to various type of denial of service attacks as they occur.
• They prevent viruses, worms, and Trojans from infecting host computers and servers.
• They enable encryption and authentication of confidential data communications.
34.

Refer to the exhibit. The network administrator of the building in the graphic needs to choose the type of cable best suited to add ServerB to the network. Which cable type is the best choice?
• STP
• UTP
• coaxial
• fiber optic
35. What is used by a routing protocol to determine the best path to include in the routing table?
• Convergence time
• Default distance
• Metric
• Type of router
36.

Refer to the exhibit. Which IP addresses could be assigned to the hosts in the diagram? (Choose two.)
• 192.168.65.31
• 192.168.65.32
• 192.168.65.35
• 192.168.65.60
• 192.168.65.63
• 192.168.65.64
37.

Given the network 192.168.25.0 shown in the graphic, which subnet mask would accommodate the number of hosts in each subnet?
• 255.255.0.0
• 255.255.224.0
• 255.255.255.0
• 255.255.255.224
• 255.255.255.240
• 255.255.255.248
38. Which two protocols allow network devices to report their status and events to a centralized network management device? (Choose two.)
• Syslog
• Telnet
• HTTP
• HTTPS
• SNMP
39. What is true regarding the differences between NAT and PAT?
• PAT uses the word "overload" at the end of the access-list statement to share a single registered address.
• Static NAT allows an unregistered address to map to multiple registered addresses.
• Dynamic NAT allows hosts to receive the same global address each time external access is required.
• PAT uses unique source port numbers to distinguish between translations.
40.

Refer to the exhibit. The graphic shows the output of a command issued on router RTB. According to the output, what two statements are true of router RTB? (Choose two.)
• The router is connected to a router named Boise.
• Router RTB is connected to a Cisco 1841 router.
• Router RTB is directly connected to two other routers.
• The IP address of the router interface connected to router RTB is 192.168.2.6 .
• The RTB router is connected to two Cisco devices by Fast Ethernet links.
41.

Refer to the exhibit. The network administrator uses the command below to configure a default route to the ISP network : RTB(config)# ip route 0.0.0.0 0.0.0.0 10.1.1.6 A ping issued from the ISP is successful to router RTB. However, ping echo request packets arrive at a host that is attached to the Fa0/0 interface of RTB, and the replies do not make it back to the ISP router. What will fix this problem?
• The ISP must be configured to forward packets from the 192.168.1.0 network.
• The ip route command needs to be edited so that the next hop address is 10.1.1.5.
• The ip route command needs to be edited so that the 192.168.1.1 address is the next hop address.
• The ip route command should be removed from the RTB router configuration.
42. A network technician is using a network management station to gather data about the performance of devices and links within the ISP. Which application layer protocol makes this possible?
• SNMP
• FTP
• DHCP
• SMTP
43. What are two purposes of DNS? (Choose two.)
• to dynamically assign IP addressing information to network hosts
• to simplify the administration of host and default gateway addressing on client computers
• to assign TCP port numbers to hosts as part of the data transfer process
• to resolve human-readable domain names to numeric IP addresses
• to replace the static HOSTS file with a more practical dynamic system
44. A hacker attempts to reach confidential information that is stored on a server inside the corporate network. A network security solution inspects the entire packet, determines that it is a threat, and blocks the packet from entering the inside network. Which security measure protected the network?
• an IDS
• an IPS
• a host-based firewall
• Anti-X software
45. How many host addresses may be assigned on each subnetwork when using the 130.68.0.0 network address with a subnet mask of 255.255.248.0?
• 30
• 256
• 2046
• 2048
• 4094
• 4096
46. In an IPv4 environment, what information is used by the router to forward data packets from one interface of a router to another?
• destination network address
• source network address
• source MAC address
• well known port destination address
47. A small tire retailer requires a low-cost WAN connection to its headquarters in order to manage its inventory and process customer sales in real time. Which WAN connection type is best suited to its needs?
• Sonet
• T3
• dialup
• DSL
• leased line
48. The command copy tftp running-config has been entered on the router. What will this command do?
• copy the configuration in RAM to a server
• copy the configuration file from a server to RAM
• copy the configuration file in NVRAM to RAM
• copy the configuration file in NVRAM to a server
• copy the configuration file from a server to NVRAM
49.

Refer to the exhibit. The network administrator needs to configure the Fa0/0 interface of RTB so that hosts from RTA can connect to the server that is attached to RTB. Which two commands will the administrator use to accomplish this task? (Choose two.)
• RTB# ip address 192.168.102.98 255.255.255.248
• RTB(config-if)# ip address 192.168.102.99 255.255.255.252
• RTB(config)# ip address 192.168.102.97 255.255.255.252
• RTB(config)# no shutdown
• RTB(config-if)# no shutdown
• RTB(config-if)# ip address 192.168.102.97 255.255.255.252
50.

Refer to the exhibit. A NOC technician at an ISP enters the command shown. What are two reasons to use this command? (Choose two.)
• to map the path to 192.168.1.7
• to test reachability to 192.168.1.7
• to locate connectivity problems along the route to 192.168.1.7
• to identify the ISPs that interconnect the NOC with the remote host with the address 192.168.1.7
• to measure the time that packets take to reach 192.168.1.7 and return to the technician's workstation
Subscribe to:
Posts (Atom)